How to Remove Trojan.Poweliks.C
 Trojan.Poweliks.C is malware that writes malicious JavaScript code directly into the Run key in the system registry. Once installed, the malicious code is executed with every system reboot. The Trojan injects the code launched from the Run registry key into the process “dllhost.exe”.
Trojan.Poweliks.C is malware that writes malicious JavaScript code directly into the Run key in the system registry. Once installed, the malicious code is executed with every system reboot. The Trojan injects the code launched from the Run registry key into the process “dllhost.exe”.
Manual Removal Guide for Trojan.Poweliks.C
Note. This is a self-help guide. Use it at your own risk. This article is provided "as is" and to be used for information purposes.
1. Before starting, make sure you are logged as a system administrator. Also, save a copy of your important files to an external hard drive/cloud storage.
2. Terminate all instances of the “dllhost.exe” process, as they contain the Trojan’s injected code:
• Right click on your taskbar, choose ‘Task Manager’ from the context menu, and:
Win7/WinXP users: Please make sure that a box ‘Show processes from all users’ is checked;
Win8 users: please click on ‘More details’ button to view all the Task Manager tabs;
• In the ‘Processes’ tab sort you tasks by name, and end all the ‘dllhost.exe’ instances by right-clicking each one and choosing ‘End Task (Process)’ from the context menu.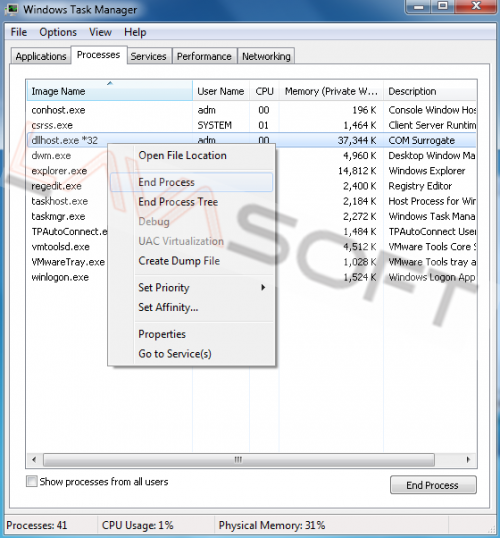
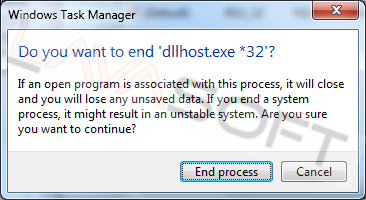
Note: If you have trouble terminating the processes try the below instructions:
• Launch command line: press Win+R keys on your keyboard, type cmd in the opened window and press ‘Enter’;
• Open one of the following folders (depending on your system) using cmd:
C:\Windows\SysWOW64 (for 64-bit OS)
C:\Windows\System32 (for 32-bit OS)
• Type the following command in the window and press ‘Enter’ to take ownership:
takeown /f dllhost.exe /a (make sure that all the spaces are observed);
• Type the following command and press enter to disable permissions:
cacls dllhost.exe /p everyone:n
• Restart your PC.
3. Open the registry and locate the below key:
"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run"
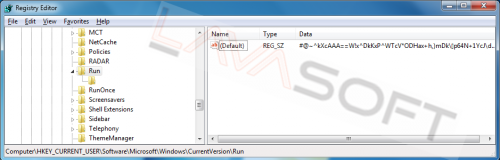
Double click on "(Default)" value and remove all the Value data by highlighting the data and pressing ‘Delete’:
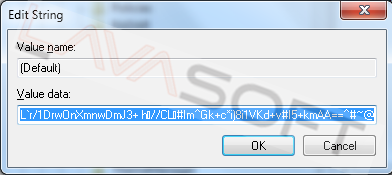
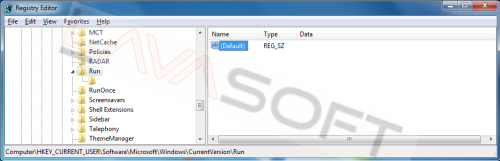
Close the Registry Editor and reboot the computer.
4. Install Ad-Aware to scan for any additional system compromises:
• Click here to download Ad-Aware, and follow installation instructions from Ad-Aware User Guide (‘Installation and Uninstallation’ -> ‘Ad-Aware Install’ section).
• Perform a full scan of your PC with Ad-Aware (following Ad-Aware User guide: ‘Scanning System’ -> ‘Running a scan’ section).
It is highly recommended to always keep your antivirus program up-to-date with a real-time protection turned on, and perform weekly full scans to stay protected at all times.




