Potentially Unwanted Program Self-Protection Technologies
Last month we discussed potentially unwanted programs that use rootkit components to protect some of their files and registry keys against modification and removal.
This month we will illustrate other self-protection methods that complicate removal and/or disabling potentially unwanted applications.
We analyzed Hometab and found that it prevents users from disabling its Browser Helper Object (BHO) in Internet Explorer. It sets the following value in the system registry:
[HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Policies\Ext\CLSID]
"{5c75ddfa-a092-4470-8dad-265d257351aa}" = "1"

This means a user cannot disable the BHO component from Internet Explorer’s Manage Add-ons menu:
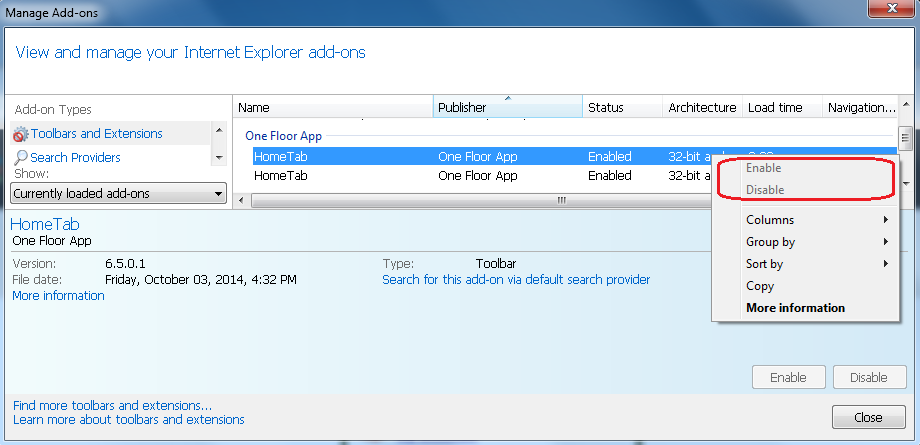
Typically, a BHO asks for permission before being enabled. However, Hometab doesn’t ask for permission to be enabled. It accomplishes this by adding a CLSID sub key to the following registry key:
[HKEY_USERS\Software\Microsoft\Internet Explorer\ApprovedExtensionsMigration\ {5c75ddfa-a092-4470-8dad-265d257351aa}]
If you see the disabled “Disable” button you can be sure this was made intentionally by the application’s developers to confuse a user who wants to remove or disable the unsolicited add-on.
An extension from Conduit runs a special service responsible for monitoring changes to its registry keys. Once a modification is detected it will restore the changed parameter. Modifications to its settings cannot be made until the watchdog service is stopped.
To illustrate, the Internet Explorer search scope setting is called “trovi-search”, which is located in the following registry key:
[HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\SearchScopes\{014DB5FA-EAFB-4592-A95B-F44D3EE87FA9}]
In theory, it can be disabled from Internet Explorer’s Add-On Manager:


However, after restarting Internet Explorer the Trovi search provider has been re-enabled.
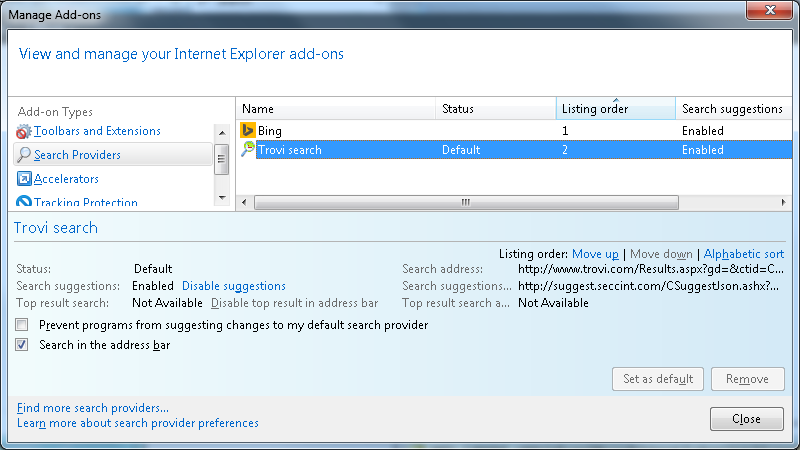
The same is true if we manually delete the corresponding Search Scope registry key from the system registry:
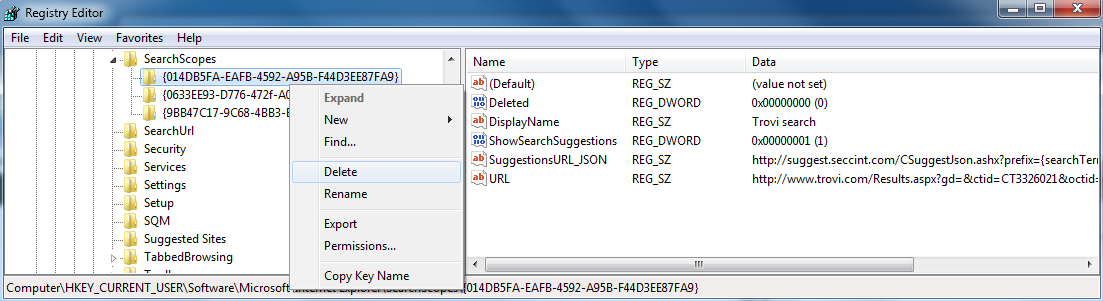
It will be restored after Internet Explorer restarts.
The service is called CltMngSvc and has the following description:

And the Search Protector (SPPD) is registered as the driver, SPPD.sys:
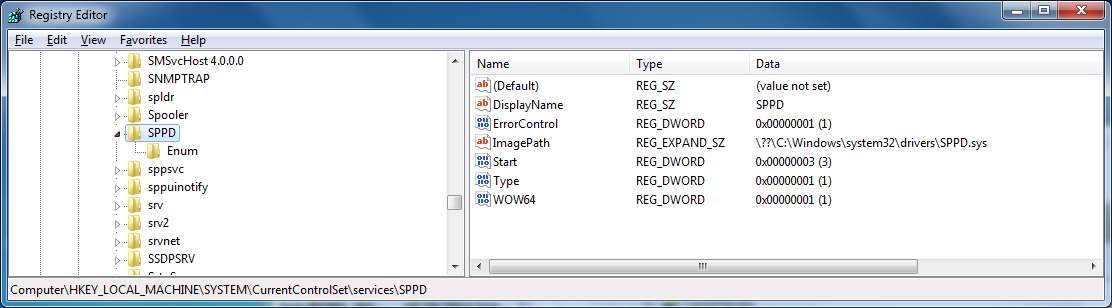
We can remove the Search provider only when the service protecting it is stopped:

After restarting Internet Explorer the Trovi search provider’s search suggestions are disabled.

The technique used by the PUP involves injecting its DLL (SPVC32.dll) into Internet Explorer’s processes (iexplore.exe) via the service process (CltMngSvc.exe):
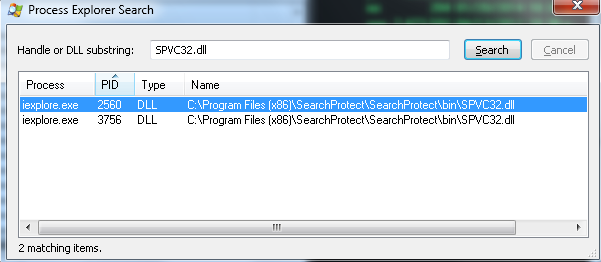
The service manager CltMngSvc.exe starts the process cltmng.exe which has pretty interesting code inside:
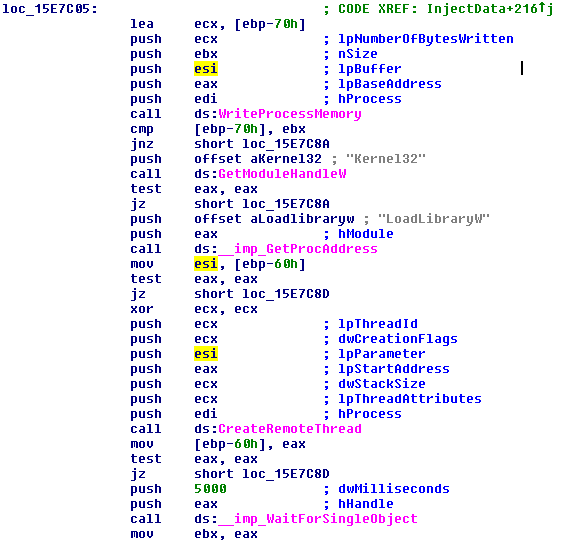
The code snippet above allows injecting the DLL into the process using a remote thread. This means the PUP does not need to be installed as Browser Helper Object in Internet Explorer - it can achieve that by injecting its DLL using the service process.
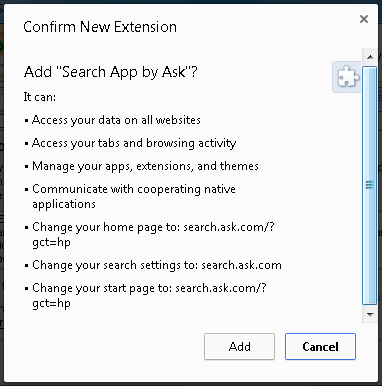
Once installed into Internet Explorer, the PUP can get full access to data submitted and transferred through the browser. Be wary of PUP extensions as they may violate the confidentiality of your private information. For example, the Chrome browser alerts a user about the potential risks of installing the PUP’s extension.
Read also:
Lavasoft Security Bulletin - October 2014: Top Threats.
Lavasoft Security Bulletin - October 2014: Bot Review.
Share this post:
 Twitter
Twitter