Lavasoft Security Bulletin: July 2013
Top20 Blocked Malware
| Position | Ad-Aware detection | % of all threats | Change in ranking |
| 1 | Win32.Trojan.Agent | 29.91% | -3.30% |
| 2 | Trojan.Win32.Generic!BT | 24.50% | -2.39% |
| 3 | Backdoor.Win32.VB.lvn | 10.20% | new |
| 4 | INF.Autorun | 2.96% | +2.18% |
| 5 | Virus.Win32.Sality.at | 2.65% | -0.58% |
| 6 | Win32.Backdoor.Inject/C | 2.50% | new |
| 7 | Worm.Win32.Taterf.b | 2.12% | new |
| 8 | Trojan.Win32.Generic.pak!cobra | 2.11% | -1.63% |
| 9 | Malware.JS.Generic | 1.99% | -0.76% |
| 10 | Trojan-Dropper.Win32.Agent | 1.81% | new |
| 11 | Virus.Win32.Sality.ek | 1.63% | new |
| 12 | Virus.Win32.Neshta.a | 1.20% | +0.51% |
| 13 | HackTool.Win32.Keygen | 1.10% | -0.52% |
| 14 | Virus.Win32.Ramnit.b | 1.06% | +0.03% |
| 15 | Virus.Win32.Virut.ce | 0.90% | +0.17% |
| 16 | Virus.VBS.Ramnit.a | 0.90% | -0.19% |
| 17 | Virus.Win32.Sality.ah | 0.87% | +0.18% |
| 18 | Trojan.Win32.Generic!SB.0 | 0.43% | new |
| 19 | Trojan.Win32.Jpgiframe | 0.34% | -0.49% |
| 20 | Heur.HTML.MalIFrame | 0.32% | -0.25% |
The Top 20 malicious programs blocked on PCs
July sees a new leader in the Top 20, Backdoor.Win32.VB.lvn detection, written in Visual Basic. The malware provides an attacker with access to the compromised system.
A detection for autorun.inf, INF.Autorun, takes the forth position. The file is used by worms to spread. In July, Ad-Aware detected and disinfected an increased number of these infections.
New apperances include Trojan.Win32.Generic!SB.0 and a modification of Sality, Virus.Win32.Sality.ek, previously examined in the first Lavasoft whitepaper published in March 2012.
Win32.Backdoor.Inject, discussed previously in a Lavasoft whitepaper published in January 2013, is a generic detection for malicious programs which inject malicious code into running processes. The injected code is used by attackers to get access to the compromised system.
Worm.Win32.Taterf.b is a worm spread through all logical, network and removable drives and is capable of disabling antivirus services. Its main payload is stealing online game users’ data, for games such as Age of Conan, Online Pool, Chain of Command and Knight Online.
During the summer, online game users are frequently the target for malware authors. This can be explained by the fact that vacation time sees an increase in online gaming activity.
Trojan-Dropper.Win32.Agent is a detection for Trojan programs which install other malicious programs as well as potentially unwanted software on the system.
New Incomings to the Lab
Let’s review and consider information on the number of unique files with the same detection name.
| Position | Ad-Aware detection | % of all threats | Change in ranking |
| 1 | Trojan.Win32.Generic!BT | 36.22% | +0.48% |
| 2 | Trojan.Win32.Generic.pak!cobra | 4.58% | +2.27% |
| 3 | Virus.Win32.Expiro.bc | 3.18% | -0.72% |
| 4 | Trojan-Downloader.Win32.LoadMoney.s | 2.71% | new |
| 5 | Trojan.Win32.Generic!SB.0 | 1.06% | -0.54% |
| 6 | Trojan.Win32.PSW.gz | 0.98% | -0.24% |
| 7 | Trojan-Dropper.Win32.Gepys.a | 0.81% | new |
| 8 | Virus.Win32.Virut.ce | 0.77% | -1.64% |
| 9 | Trojan.JS.Obfuscator.aa | 0.59% | -0.11% |
| 10 | Win32.Malware!Drop | 0.48% | +0.15% |
| 11 | Trojan.Win32.Vobfus.paa | 0.42% | +0.07% |
| 12 | Worm.Win32.Pykspa | 0.40% | new |
| 13 | FraudTool.Win32.FakeRean | 0.39% | +0.05% |
| 14 | Worm.Win32.Gamarue.aa | 0.38% | +0.03% |
| 15 | Trojan.Win32.Autorun.dm | 0.32% | new |
| 16 | Trojan.Win32.Qhosts.bf | 0.31% | -0.04% |
| 17 | Malware.JS.Generic | 0.31% | -0.04% |
| 18 | TrojanPWS.Win32.OnLineGames.ahj | 0.30% | -0.05% |
| 19 | Trojan.Win32.Dwnldr.y | 0.28% | -0.08% |
| 20 | Worm.Win32.Mabezat.b | 0.27% | -0.69% |
New malicious programs entered the Top 20
July sees four new detections in the Top 20. Worm.Win32.Pykspa, discussed previously in a Lavasoft whitepaper published in April 2013; Trojan.Win32.Autorun.dm, which entered the Top 20 for the first time in August 2012 is designed to automatically run malicious programs; Trojan-Downloader.Win32.LoadMoney and Trojan-Dropper.Win32.Gepys.a.
Trojan-Downloader.Win32.LoadMoney.s is a Trojan program which installs other malicious programs on the compromised system without user’s knowledge. Mail.ru previously used a downloader that installed the Mail.ru.Guard and Mail.ru.Sputnik utilities without user’s knowledge. Some antivirus vendors detected this malicious program as "not-a-virus LoadMoney". We categorise such programs as “Trojan” because it is unacceptable for legal software to install a program without user’s knowledge.
Trojan-Dropper.Win32.Gepys.a is a Trojan that installs other malicious programs on the system. As a rule, it is a dynamic link library (DLL) saved in the "All Users" profile to the %AppData%\Mozilla folder under a randomly generated name. The automatic launch of a DLL at each running process is caused by changes to the "AppInit_DLLs" system registry key:
[HKLM\Software\Microsoft\Windows NT\CurrentVersion\Windows]
Fake antiviruses holding machines to ransom until a fee is paid to unlock their computers continue to blight users. In July, our systems detected the following fake antiviruses:

Fake AV (MD5: 5a88b972fcf39d2f5b0fb941b76f54c6) is detected by Ad-Aware as Trojan.Win32.FakeAV.IS

Fake AV (MD5: 7b8763eb682cef61090c7eeb3f6e408d) is detected by Ad-Aware as Trojan.Win32.Jorik.Fraud.un
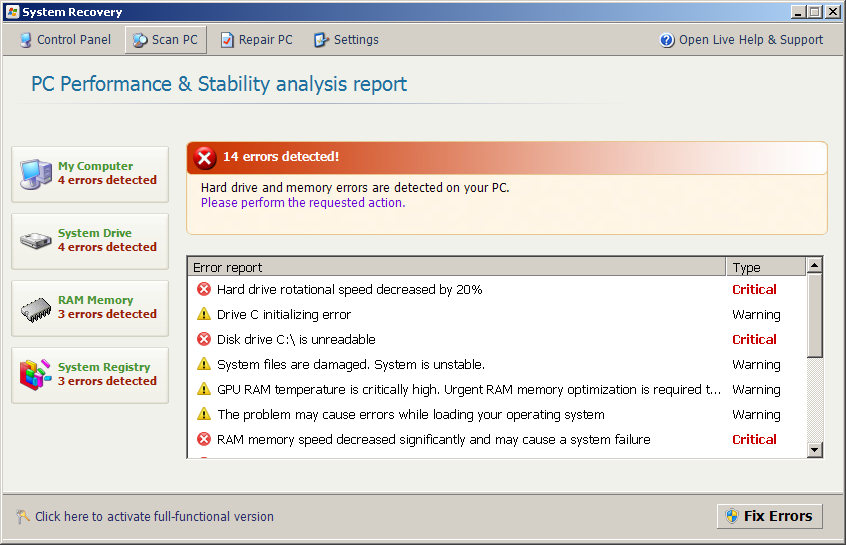
Fake AV (MD5: 51f39bed9b38cd74ce3020e9e7b9730f) is detected by Ad-Aware as Trojan.Win32.FakeAv.awrp
Undocumented FPU instructions
In June, Microsoft published the results of its investigation into a new undocumented instruction trick AlienVault Labs subsequently published "Hunting for malware with undocumented instructions". The following malware samples use FPU instructions that lead to incorrect disassembly in several debuggers and disassemblers: Backdoor:Win32/Farfli.AV, Trojan:Win32/Danglo, Backdoor:Win32/Zegost.B were detected.
Based on a Yara rule from AlienVault Labs, in July, we added the following Yara rule to Lavasoft MAS:
rule undocumentedFPUinstructions
{
strings:
$a1 = {D9 D8}
$a2 = {DF DF}
condition:
($a1 in (entrypoint..entrypoint+12)) or ($a2 in (entrypoint..entrypoint+12)) or (for any of ($a*) : ($ at entrypoint))
}
Our automated analysis systems detected the following samples:

MD5: 0f66f960852d1c9fb184e4813143aa90, detected by Ad-Awar as Trojan.Win32.Bdoor.bdk, detected by Microsoft as Backdoor:Win32/Zegost.AD

MD5: 5eb3a32051320dc1b3caa6e554a54ffb, detected by Ad-Aware us Trojan.Win32.Generic!BT, detected by Microsoft asBackdoor:Win32/Racdr.A

MD5: 011d1e05bb63314922936d02b63a7a93, detected by Ad-Aware us Trojan.Win32.Generic!BT, detected by Microsoft as DDoS:Win32/Nitol.A

MD5: cf9ee9be74908e1c8c3b2ee607812743, detected by Ad-Aware us Trojan.Win32.Generic!BT, detected by Microsoft as Backdoor:Win32/Babmote.A

MD5: e2bdc9e611a6cbe3f637165dcd14990c, detected by Ad-Aware us Trojan.Win32.Redosdru.C, detected by Microsoft as Backdoor:Win32/Babmote.A
All files, apart from DDoS:Win32/Nitol.A were not packed. DDoS:Win32/Nitol.A was packed by RLPack. Attackers might use special means to add those instructions to the executable files after compiling and packing. We tried to reproduce attackers’ actions experimenting with a legitimate file, notepad.exe, by modifying an entry point:

MD5: 394f5fd5696cca3648a53a179da66059
Afterwards, the file was uploaded to virustotal.com:

Two antivirus vendors added detection of undocumented instructions even in white files. The trick can be used by attackers to counteract emulators of antivirus companies.
Tandem-type IRC Bots
In July, an interesting infection incident was detected by our automated malware analysis system, Lavasoft MAS. Three IRC bots were simultaneously detected on the compromised system: Nrbot, Blazebot and Rbot.
Two C&C servers were detected from which commands can be received by Nrgbot (channel #nrz#), Rbot(channel #fkyou# ) and Blazebot (channel ##TBT). The auto-join channel "#Security-Check" for all bots:
178.33.232.15
146.82.5.222
By using Internet Relay Chat client mIRC and connecting to C&C servers, it is possible to track the current commands bots receive. When the description was created, the same commands were received from two servers:


Attackers again show an interest in Bitcoin. With malicious programs such as Skyper attackers can install a bitcoin generator on compromised computers. For this time, attackers went on and organize a tandem with IRC bots.
Top20 Potentially Unwanted Programs
Below are the Top20 Potentially Unwanted Programs blocked by Ad-Aware on user’s PCs. These are advertising software, browser toolbars, search engines and other programs which change browser start pages and other system settings.
| Position | Ad-Aware detection | % of all threats | Change in ranking |
| 1 | MyWebSearch | 26.24% | +6.12% |
| 2 | Adware.Linkury | 14.95% | -4.84% |
| 3 | Win32.Toolbar.Iminent | 8.43% | -2.15% |
| 4 | Win32.PUP.Bandoo | 7.84% | +1.29% |
| 5 | SweetIM | 4.56% | -1.87% |
| 6 | Iminent | 4.51% | -6.07% |
| 7 | Bprotector | 3.18% | -0.93% |
| 8 | InstallCore | 2.26% | -0.02% |
| 9 | Yontoo | 2.17% | -0.98% |
| 10 | Babylon | 1.70% | -0.13% |
| 11 | Artua Vladislav | 1.35% | -0.19% |
| 12 | InstallBrain | 1.34% | -0.01% |
| 13 | Win32.Adware.ShopAtHome | 1.29% | +0.40% |
| 14 | Wajam | 1.27% | -0.01% |
| 15 | DownloadMR | 1.22% | +0.07% |
| 16 | CoolMirage Ltd | 1.05% | -0.01% |
| 17 | DomaIQ | 1.00% | -1.18% |
| 18 | Optimum Installer | 0.88% | +0.07% |
| 19 | Win32.Toolbar.Mediabar | 0.78% | -0.03% |
| 20 | GamePlayLabs | 0.75% | -0.38% |
Top20 PUPs detected on user’s PC
Operating Systems

Infections by OS
Geographic Location

Infections by country of origin
We will keep investigating the epidemiological situation in the world and informing our readers about new malicious code samples in the next Lavasoft Security Bulletin.
Share this post:
 Twitter
Twitter