Lavasoft Security Bulletin: August 2013
Top20 Blocked Malware
| Position | Ad-Aware detection | % of all threats | Change in ranking |
| 1 | Win32.Trojan.Agent | 30.04% | +0.13% |
| 2 | Trojan.Win32.Generic!BT | 25.85% | +1.35% |
| 3 | Email-Worm.Win32.Brontok.a | 3.79% | new |
| 4 | Trojan.Win32.Generic.pak!cobra | 2.90% | +0.79% |
| 5 | Virus.Win32.Sality.at | 1.27% | -1.38% |
| 6 | Malware.JS.Generic | 1.22% | -0.77% |
| 7 | HackTool.Win32.Keygen | 1.14% | +0.04% |
| 8 | Virus.Win32.Ramnit.b | 1.00% | -0.06% |
| 9 | Trojan.Win32.Gframe | 0.66% | new |
| 10 | Virus.Win32.Neshta.a | 0.58% | -0.62% |
| 11 | Worm.Win32.Pykspa | 0.50% | new |
| 12 | Heur.HTML.MalIFrame | 0.38% | +0.06% |
| 13 | Virus.Win32.Sality.ah | 0.38% | -0.49% |
| 14 | Trojan.Win32.Jpgiframe | 0.36% | +0.02% |
| 15 | Trojan.Win32.Generic!SB.0 | 0.28% | -0.15% |
| 16 | Trojan.Win32.Clicker!BT | 0.27% | new |
| 17 | Trojan.Win32.Sirefef.bb | 0.27% | new |
| 18 | INF.Autorun | 0.24% | -2.72% |
| 19 | Trojan-Clicker.HTML.Iframe | 0.24% | new |
| 20 | Trojan.Win32.Startpage.or | 0.22% | new |
The Top 20 malicious programs blocked on PCs
August sees new detections in the Top 20 while Email-Worm.Win32.Brontok.a and Worm.Win32.Pykspa make a return to the prevalence list having last been seen in June 2013 and April 2013, Trojan.Win32.Gframe, detecting malicious IFrames embedded in GIF files, makes an appearance at position nine.

Trojan.Win32.Gframe (MD5: ffd89e57a371bec38a249354be8fff0e)
New Incomings to the Lab
Let’s review and consider information on the number of unique files with the same detection name.
| Position | Ad-Aware detection | % of all threats | Change in ranking |
| 1 | Trojan.Win32.Generic!BT | 35.47% | -0.75% |
| 2 | Trojan.Win32.Generic.pak!cobra | 4.76% | +0.18% |
| 3 | Virus.Win32.Expiro.bc | 4.07% | +0.89% |
| 4 | Trojan-Downloader.Win32.LoadMoney.u | 4.06% | new |
| 5 | Virus.Win32.Virut.ce | 2.90% | +2.13% |
| 6 | Worm.Win32.Gamarue.aa | 1.26% | +0.88% |
| 7 | Trojan.Win32.Desini.a | 1.00% | new |
| 8 | Malware.JS.Generic | 0.99% | +0.68% |
| 9 | Trojan-Dropper.Win32.Gepys.a | 0.85% | +0.04% |
| 10 | Trojan.Win32.Generic!SB.0 | 0.81% | -0.25% |
| 11 | Win32.Malware!Drop | 0.77% | +0.29% |
| 12 | Trojan.Win32.Runner.a | 0.71% | new |
| 13 | Trojan.Win32.Dwnldr.y | 0.66% | +0.38% |
| 14 | FraudTool.Win32.FakeRean | 0.65% | +0.26% |
| 15 | Trojan.Win32.PSW.gz | 0.61% | -0.37% |
| 16 | Trojan.JS.Obfuscator.aa | 0.55% | -0.04% |
| 17 | Trojan.Win32.Reveton.a | 0.51% | new |
| 18 | Trojan.Win32.Vobfus.paa | 0.45% | +0.03% |
| 19 | TrojanPWS.Win32.OnLineGames.ahj | 0.43% | +0.13% |
| 20 | Worm.Win32.Mabezat.b | 0.37% | +0.10% |
New malicious programs entered the Top 20
Fake antiviruses holding machines to ransom until a fee is paid to unlock their computers continue to blight users. In August, our systems detected the following fake antiviruses:

Fake AV (MD5: 54828dd3e11fc1b5401745bdb5ae4251) is detected by Ad-Aware as Trojan.Win32.Reveton.a
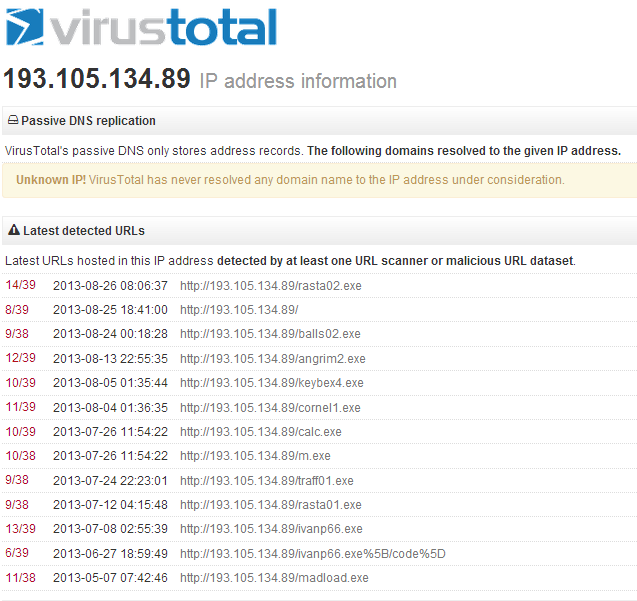
Fake AV (MD5: 8ca5e580c60e66d4c87f9aa408946fc3) is detected by Ad-Aware as Trojan.Win32.Generic!BT

Fake AV (MD5: f83ca10a393ec4759202c077d63c3a20) is detected by Ad-Aware as FraudTool.Win32.FakeAV.hdd
Another prevalent class of malware is ransomware. This month we discovered a new take on the ransom tactic, called “PRISM locker”. It tricks users by showing popups, supposedly from the “NSA”, claiming they have been caught downloading and distributing illegal content, forcing the victim to pay a fine of $300 to unlock the computer.

PRISM locker (MD5: e1988e7512bb18dc0e3ed946ca466d0f) is detected by Ad-Aware as Trojan.Win32.Generic
Once launched the Trojan adds a reference to the registry Run key ensuring the infected computer will be locked with the next system start up:
[HKCU\Software\Microsoft\Windows\CurrentVersion\Run]
"internat.exe"
You can find more details about that malware here.
New Features of Kelihos
Recently we published a report on Kelihos Update, where we presented new app targets and installation features in the backdoor. The paper also revealed that the botnet was still in operation and all six job servers were up and running.
Thanks to VirusTotal we can see several cached requests to the Kelihos job server:
The most remarkable change was in the installation procedure. Previous versions added “SonyAgent” values in a system registry:
[HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"SonyAgent"="
[HKCU\Software\Sony]
"SonyID"="DCmkXuRtjruvB1iHVBkEJlW2S+BimFp/lF4WuQjFyUZiEEBn51H4u+8OsvFwcsEfxA=="
"SonyID1"=dword:00000050
"SonyID2"=hex:00,00,00,00,00,00,00,00
"SonyID3"= (data_in_hex)
This time it uses randomization for registry entries and filenames, which complicates recognizing the infection for an ordinary user. The backdoor tries to mimic names of system files and services:
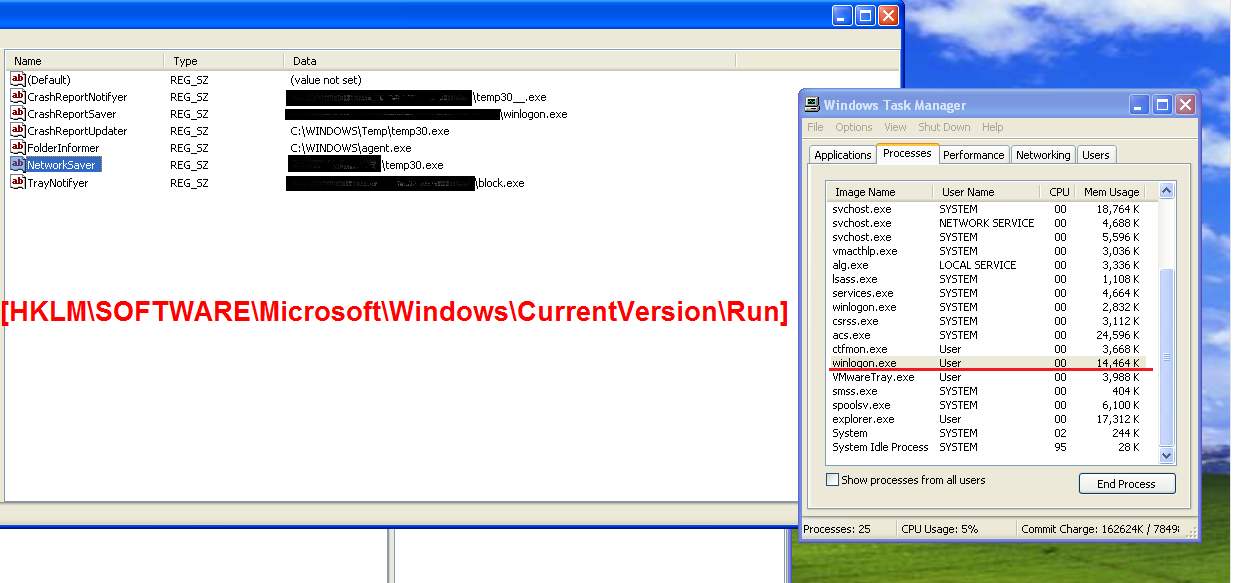
Kelihos uses random names from the list when spreading via removable drives by creating its copies and lnk files:
X:\{password, screensaver, click, installer, hentai, run, porn, game}.exe
X:\Shortcut to %file name from the list%.lnk
The additional dummy user-agents are used to avoid blocking http connections. The number of fake agents increased from 28 to 47 since March.
There are new incomings among targeted applications where the backdoor looks for user credentials as well:
Cyberduck, FreshFTP, FTPShell, Global Downloader, Notepad++, TFTPInfo, MyFTP, Sherrod, NovaFTP, CoolNovo
We scanned again fast-flux network for “ditojtap.ru” and harvested 4543 IP addresses that help to deliver updates to zombie computers.
It looks pretty similar to the map built for 6244 proxy-bots in March:
Both maps reveal that Ukraine is the most affected country with 47% of infected computers in the botnet’s fast-flux network.
The VirusTotal cached some of the DNS requests:
The main finding is that the botnet is still in operation despite all attempts to take it down. You can find a description of the latest downloaded sample in our Malware Encyclopedia.
Top20 Potentially Unwanted Programs
Below are the Top20 Potentially Unwanted Programs blocked by Ad-Aware on user’s PCs. These are advertising software, browser toolbars, search engines and other programs which change browser start pages and other system settings.
| Position | Ad-Aware detection | % of all threats | Change in ranking |
| 1 | MyWebSearch | 4.54% | -21.70% |
| 2 | Adware.Linkury | 1.52% | -13.43% |
| 3 | Win32.PUP.Bandoo | 1.33% | -6.51% |
| 4 | Win32.Toolbar.Iminent | 1.06% | -7.37% |
| 5 | Iminent | 0.49% | -7.94% |
| 6 | Bprotector | 0.42% | -2.76% |
| 7 | SweetIM | 0.40% | -4.16% |
| 8 | InstallCore | 0.37% | -1.89% |
| 9 | Yontoo | 0.25% | -1.92% |
| 10 | Win32.Adware.ShopAtHome | 0.22% | -1.07% |
| 11 | Wajam | 0.19% | -1.08% |
| 12 | CoolMirage Ltd | 0.18% | -0.87% |
| 13 | ExpressFiles Installer | 0.17% | new |
| 14 | DownloadMR | 0.16% | -1.06% |
| 15 | AirInstaller | 0.16% | new |
| 16 | Artua Vladislav | 0.15% | -1.20% |
| 17 | Babylon | 0.15% | -1.55% |
| 18 | DomaIQ | 0.14% | -0.86% |
| 19 | InstallBrain | 0.13% | -1.21% |
| 20 | Win32.Toolbar.Mediabar | 0.13% | -0.65% |
Top20 PUPs detected on user’s PC
Operating Systems

Infections by OS
Geographic Location

Infections by country of origin
We will keep investigating the epidemiological situation in the world and informing our readers about new malicious code samples in the next Lavasoft Security Bulletin.
Share this post:
 Twitter
Twitter