Lavasoft Security Bulletin: April 2013
Top20 Blocked Malware
| Position | Ad-Aware detection | % of all threats | Change in ranking |
| 1 | Win32.Trojan.Agent | 30.54% | +3.56% |
| 2 | Trojan.Win32.Generic!BT | 27.12% | -2.01% |
| 3 | Trojan.Win32.Generic.pak!cobra | 2.95% | -0.46% |
| 4 | Virus.Win32.Sality.r | 2.44% | new |
| 5 | Trojan.Win32.AutoIt.gen.1 | 2.36% | new |
| 6 | Virus.Win32.Sality.at | 2.09% | -0.41% |
| 7 | Malware.JS.Generic | 2.04% | -0.17% |
| 8 | Virus.Win32.Sality.ah | 1.72% | +0.27% |
| 9 | Email-Worm.Win32.Brontok.a | 1.42% | +0.64% |
| 10 | Virus.Win32.Sality.am | 1.25% | new |
| 11 | Virus.Win32.Ramnit.b | 1.07% | +0.48% |
| 12 | Worm.Win32.Pykspa | 1.01% | new |
| 13 | Virus.Win32.Ramnit.a | 0.98% | +0.15% |
| 14 | INF.Autorun | 0.90% | -0.23% |
| 15 | Trojan.Win32.Ramnit.c | 0.86% | -1.26% |
| 16 | Virus.VBS.Ramnit.a | 0.83% | -2.09% |
| 17 | HackTool.Win32.Keygen | 0.81% | -0.22% |
| 18 | Trojan.Win32.Sirefef.bb | 0.70% | +0.12% |
| 19 | Trojan.Win32.Jpgiframe | 0.43% | -0.43% |
| 20 | Heur.HTML.MalIFrame | 0.27% | -0.29% |
The Top 20 malicious programs blocked on PCs
April sees a position change for the most prevalent generic detections: Trojan.Win32.Generic!BT and Win32.Trojan.Agent. Compared to March, new modifications of Sality Virus.Win32.Sality.r and Virus.Win32.Sality.am entered the Top 20 at positions 4 and 10 respectively. A new generic detection for Trojans written in the AutoIt script language – Trojan.Win32.AutoIt.gen.1 – entered the Top 20. A new Worm.Win32.Pykspa, a worm that can provide an attacker remote access to a compromised system, also appears in the Top 20. The worm spreads via Skype, Twitter network shares and removable drives, prevents users from visiting internet resources belonging to antivirus companies, and ends processes belonging to various utilities for diagnosing infected system,including antivirus products.
New Incomings to the Lab
Let’s review and consider information on the number of unique files with the same detection name.
| Position | Ad-Aware detection | % of all threats | Change in ranking |
| 1 | Trojan.Win32.Generic!BT | 36.37% | +6.61% |
| 2 | Trojan.Win32.Generic.pak!cobra | 3.57% | +1.05% |
| 3 | Virus.Win32.Expiro.bc | 1.70% | -0.06% |
| 4 | Virus.Win32.Virut.ce | 1.59% | +0.21% |
| 5 | Trojan.Win32.Medfos.m | 1.35% | -0.05% |
| 6 | Trojan.Win32.Dwnldr.y | 1.29% | -0.01% |
| 7 | Worm.Win32.Mabezat.b | 0.57% | +0.22% |
| 8 | Trojan.JS.Obfuscator.aa | 0.56% | +0.11% |
| 9 | Trojan.Win32.Winwebsec.fd | 0.54% | -0.02% |
| 10 | Trojan.Win32.Vobfus.paa | 0.49% | -0.00% |
| 11 | Malware.JS.Generic | 0.48% | +0.1% |
| 12 | Virus.Win32.PatchLoad.d | 0.41% | +0.08% |
| 13 | Win32.Malware!Drop | 0.41% | +0.17% |
| 14 | Trojan.JS.IFrame.i | 0.37% | +0.00% |
| 15 | Trojan.Win32.Generic!SB.0 | 0.29% | +0.05% |
| 16 | Trojan.Win32.Tepfer.a | 0.24% | -0.19% |
| 17 | TrojanPWS.Win32.OnLineGames.ahj | 0.24% | new |
| 18 | Trojan.Win32.Autorun.dm | 0.19% | +0.02% |
| 19 | Trojan-PWS.Win32.Zbot.aql | 0.20% | +0.00% |
| 20 | Trojan.Win32.Urelas.a | 0.18% | new |
New malicious programs entered the Top 20
April sees two new families, TrojanPWS.Win32.OnLineGames.ahj and Trojan.Win32.Urelas.a, at position 17 and 20 respectively.
TrojanPWS.Win32.OnLineGames.ahj is a dynamic-link library (DLL). It is an Internet Explorer Browser Helper Object (BHO) that is run when Internet Explorer launches. It collects data users enter on online game web sites sending the stolen data to attackers’ servers.
Trojan.Win32.Urelas.a provides an attacker with remote access to the infected computer. Taking commands from the CC server, the Trojan downloads its updates and other malicious programs, steals user’s confidential data, and collects information about the system.
This month our automatic analysis system detected an increase of ransom Trojans among Trojan.Win32.Generic!BT generic detections. Let’s consider some of them as well as options for manually removing these threats from the infected computer.
Example 1. This is what the malicious program preventing the computer from performing properly looks like:

Ransomware (MD5: 627e226a5924634651c264f033b1ba33) is detected by Ad-Aware as Trojan.Win32.Generic!BT
The Trojan is easily removed in Windows Safe Mode. The Trojan body needs to be removed from the current user's Windows directory:
%Documents and Settings%\%CurrentUser%\%AppData%\top1.exe
As well as autorun registry key:
[HKCU\Software\Microsoft\Windows\CurrentVersion\Run]
"top" = "%Documents and Settings%\%CurrentUser%\%AppData%\top1.exe"
The attackers’ server, from which an html-page blocking the computer performance is loaded, is located in Germany:

Example 2. This is what the malicious program preventing the computer from performing properly looks like:

Ransomware (MD5: 2a1864a89a64b3617fc5f233ed3f604c) is detected by Ad-Aware as Trojan.Win32.Generic!BT
It is more complicated to remove this Trojan. This is because the Trojan makes reference to itself in a more obscure registry value:
[HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon]
"Shell" = "%Documents and Settings%\%CurrentUser%\%AppData%\Battleshield.exe"
To prevent the Trojan from launching automatically in safe mode, Windows can be started in safe mode with command line support using the following commands to remove the autorun capability:
reg delete "HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /v Shell
del "%Documents and Settings%\%CurrentUser%\%AppData%\Battleshield.exe"
The attackers’ server from which an html-page blocking the computer performance is loaded is located in Germany:

Example 3. This is how the malicious program preventing the computer from performing properly looks like:

Ransomware (MD5: b4cb159208511637ca06e78dbfb0af97) is detected by Ad-Aware as Trojan.Win32.Generic!BT
It is much complicated to remove this Trojan as attackers have made efforts to prevent deleting the malicious program in safe mode. After infection, the Trojan removes all keys from the registry branch:
[HKLM\System\CurrentControlSet\Control\SafeBoot]
This leads to BSOD when attempting to start Windows in safe mode:

The Trojan copies itself to the current user's Windows temporary folder:
%Temp%\WindowsUpdate.exe
If more than one user have access to the infected computer, it is possible to use the "Win+L" hot key to sign in Windows from different accounts. Afterwards, it is possible to remove the worm body and autorun registry key:
[HKCU\Software\Microsoft\Windows\CurrentVersion\Run]
"WindowsUpdate.exe" = "%Temp%\WindowsUpdate.exe"
And restore the registry branch:
[HKLM\System\CurrentControlSet\Control\SafeBoot]
Otherwise, it is required to use CD or USB flash drive to restore the system or cure infected HDD on another system by scanning it with an antivirus program, or manually removing the Trojan body.
The attackers’ server from which an html-page blocking the computer performance is loaded is located in UK:

Ad-Aware antivirus is capable of detecting ransom Trojans infections, as described above. If your computer is infected by ransom Trojan of this type, do not panic and pay attackers a fee to unlock your computer. It is always possible to cure your system: "Fortune favours the brave".
Skyper
In April, the activity of "Skyper" IRCBot was observed. "Skyper" used social engineering techniques to spread itself using instant messaging services:

Malware memory damp fragment
If any instant messaging software was installed on the infected computer, the malware sent messages containing a link to its body to all contacts from the list. The malware works out the locale of the infected OS and sends random phrases in the corresponding language.

Text message sample for the Italian locale
Afterwards, a link created using Goo.gl service was added to the text.
http://www.goo.gl/***?image=IMG0540240-JPG
A peculiarity of the worm is installing a module designed to launch a bitcoin generator on the infected computer. The process used for bitcoin mining calculations generates significant load on the affected machine.
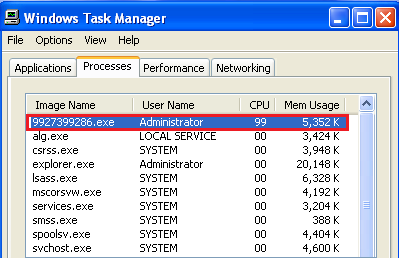
A process of malware module responsible for bitcoin generation
Attackers continue using various social engineering techniques to spread malware. This effective technique allows for the creation huge botnets. The chances are very high that someone receiving from a friend a message that contains the "You look so beautiful on this picture" text, along with a link, will click that link for sure.
Bitcoin mining remains a profitable business for attackers. Bitcoin currency rates help demonstrate this; the price of one BTC recently reached 260$. Sensing easy money, criminals surreptitiously install Bitcoin mining software on zombie machines in botnets.

Bitcoin Charts, resource: Mtgox
You can read a more detailed description of spreading techniques and payload of this malware in our Malware Encyclopedia.
Top20 Potentially Unwanted Programs
Below are the Top20 Potentially Unwanted Programs blocked by Ad-Aware on user’s PCs. These are advertising software, browser toolbars, search engines and other programs which change browser start pages and other system settings.
| Position | Ad-Aware detection | % of all threats | Change in ranking |
| 1 | MyWebSearch | 22.61% | -6.7% |
| 2 | Adware.Linkury | 18.18% | new |
| 3 | Win32.Toolbar.Iminent | 9.63% | -6.04% |
| 4 | Win32.PUP.Bandoo | 7.08% | -2.56% |
| 5 | SweetIM | 5.55% | -1.66% |
| 6 | Bprotector | 4.46% | -1.94% |
| 7 | Wajam | 2.36% | +0.42% |
| 8 | Yontoo | 2.27% | +0.04% |
| 9 | Babylon | 1.71% | -1.03% |
| 10 | 1ClickDownloader | 1.44% | new |
| 11 | InstallBrain | 1.40% | -0.5% |
| 12 | Artua Vladislav | 1.40% | -0.27% |
| 13 | DownloadMR | 1.35% | +0.05 |
| 14 | CoolMirage Ltd | 1.35% | new |
| 15 | GamePlayLabs | 1.17% | -0.12% |
| 16 | DomaIQ | 1.15% | new |
| 17 | ExpressFiles Installer | 1.11% | new |
| 18 | Win32.Adware.ShopAtHome | 1.10% | -0.44% |
| 19 | BetterInstaller | 1.10% | new |
| 20 | Click run software | 1.0% | -0.37% |
Top20 PUPs detected on user’s PC
Operating Systems

Infections by OS
Geographic Location

Infections by country of origin
We will keep investigating the epidemiological situation in the world and informing our readers about new malicious code samples in the next Lavasoft Security Bulletin.
Share this post:
 Twitter
Twitter