The Big Three Email Nuisances: Spam, Phishing and Spoofing
 We have to admit that cyber criminals and scammers are very artistic and inventive individuals. They seem to always find a way or two in trying to trick computer users into falling to their traps.
We have to admit that cyber criminals and scammers are very artistic and inventive individuals. They seem to always find a way or two in trying to trick computer users into falling to their traps.
For most of us, these three terms seem to denote the same thing. However, they are very different from each other. Let’s take a look at their definitions.
Spam
Also known as unsolicited bulk e-mail messages or any email messages irrespective of content that is unwanted or unrequested by the recipient. Spam messages are mostly commercial advertising, although chain letters, political mailings and other forms of non-commercial mailings are often included under the same categorization. A large portion of spam has also been found to be comprised of ads for products of dubious quality and services of questionable legality.
There are two types of spam: intentional and unintentional.
- Intentional spam comes from spammers who are soliciting products or attempting to commit fraud.
- Unintentional spam originates from computers that are infected with a virus or worm that activates e-mail distribution processes in the background. The virus or worm attempts to send bulk messages from the infected computer without the awareness of the computer owner.
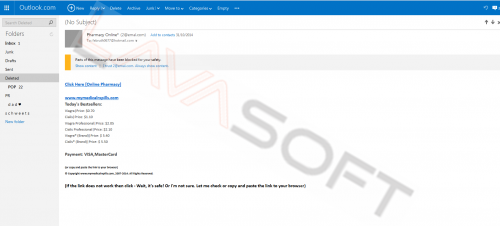
Here are a few examples of spam emails.
Please click on the images to enlarge.
Phishing
Phishing is a special type of spam that is intended to trick you into entering your personal or account information for the purpose of breaching your account and committing identity theft or fraud.
Typically, a false e-mail message is delivered to you. The e-mail appears to come from a legitimate source, for example eBay, your bank, government departments etc. The message may contain a legitimate corporation's logo, and appear to be sent from the corporation's e-mail address. The message may ask you to click a link in the message to update your account, or run a software program to upgrade your computer.
Although the message looks legitimate, it is really trying to compel you to submit your personal and confidential information, which will be used to steal your credentials. Normally you are asked to enter information such as your name, date of birth, place of birth, social security number, mother's maiden name, bank account number, and bank account PIN. Web sites that are frequently spoofed by phishers include PayPal, eBay, MSN, Yahoo, BestBuy, and America Online.
The following screen shots are of a "phishing" email pretending to be from PayPal. This email was not sent by PayPal, rather by someone trying to collect sensitive data in a very tricky fashion. Descriptions relating to each screen shot are listed below.
Please click on the images to enlarge.
Source: Pon Net
Spoofing
Spoofing is the forgery of an e-mail header so that the message appears to have originated from someone or somewhere other than the actual source. Spoofing is often used by spammers and can be accomplished by changing your "FROM" e-mail address.
E-mail spoofing may occur in different forms, but all have a similar result: a user receives email that appears to have originated from one source when it actually was sent from another source. E-mail spoofing is often an attempt to trick the user into making a damaging statement or releasing sensitive information, such as a password. E-mail spammers often use spoofing in an attempt to get recipients to open, and possibly even respond to, their solicitations.
To send spoofed e-mail, senders insert commands in headers that will alter message information. It is possible to send a message that appears to be from anyone, anywhere, saying whatever the sender wants it to say. Thus, someone could send spoofed e-mail that appears to be from you with a message that you didn't write.
A number of measures to address spoofing are available including: SPF, Sender ID, DKIM, and DMARC. Although their use is increasing, it is likely that almost half of all domains still do not have such measures in place. However, as of 2013, 60% of consumer mailboxes worldwide use DMARC to protect themselves against direct domain spoofing and only 8.6% of emails have no form of domain authentication.
Spam and phishing emails typically use such spoofing to mislead the recipient about the origin of the message.