How Social Networking Security Awareness Saved A Company’s Reputation

Guest post by Pierluigi Paganini from the InfoSec Institute
Social Networks: How to Boost the Company
For the majority of companies, the social networks represent a privileged instrument to improve the efficiency of their communications and increase the brand reputations. Social networks allow companies to reach a wide audience instantly, increasing the trust of customers for the company and its products.
Many businesses recognize the benefits of having a social media presence for long-term marketing purposes; however, many are not aware of social media’s security issues. Almost any organization ignores how employees’ own social presence can expose the company to cyber threats that could harm its reputation.
The reputation is the pillar for the success of any company and a proper security posture on the social networks could prevent serious damages to their image. Social media offer a huge marketing opportunity at limited costs, but it is important for companies to not underestimate the threat to their reputation.
Security experts believe that IT companies are among the most exposed entities to threats because of the young age of most of their workers, which implies a natural propensity to use social networks. As more organizations continue to jump into social media, soon a critical mass will be reached and all the other companies will be forced to adopt social media for business matter. The opening to social media by companies is a rapid process; for this reason it is crucial to address risks related to the exposure to new threats related to the new paradigm.
Social media offer important business advantages to companies, but they also dramatically enlarge their attack surface. In order to mitigate the security risks, organizations must establish and deploy effective social media usage policies. Unfortunately, in many cases, companies simply limit their action is to prohibiting the access to social media for its employees, a decision that could cause significant disadvantage of the organization respect its competitors.
Social Network and Cyber Threats … A Privileged Attack Vector
The number of cyber treats leveraging social networks is constantly increasing: According to The Symantec “Internet Security Threat Report 2015,” in 2014 70 percent of social media scams were manually shared. The principal problem related to social network scams is related to the “trust factor”; that is, victims tend to click on something posted by a friend, completely ignoring the risks.
As explained by experts at Symantec, in 2014 criminals hijacked the power of “social proof,” the principle that humans attribute more value to something if it is shared or approved by others. It is quite easy to find on social network fraud attempts that invite users to join a fake event or group with incentives such as free gift cards. Joining often requires the victims to provide their credentials or send a text to a premium rate number. The user credentials could open the door of the organization, exposing to the attackers sensitive information regarding the company and its activities. Experts at Symantec have identified the following media threats when dealing with principal social media platforms, such as Facebook, Twitter, and Pinterest:
- Manual Sharing –Victims are the main actors of the fraud scheme; they share with their contact malicious content such as videos and fake offers that redirect them to bogus domain used for phishing attacks or to serve malware.
- Fake Offering – These scams invite social network users to join a fake event or group that shares the same interests. Similar scams targeted a huge number of companies and research communities; threat actors used attractive subject to trick victims into clicking on malicious links or downloading malicious files.
- Likejacking – Using fake “Like” buttons, attackers trick users into clicking website buttons that are used by fraudsters to install malware. This attack scheme could allow an attacker also to impersonate the victim by posting updates on a user’s newsfeed. This kind of attack could be very dangerous for the company reputation.
- Comment Jacking – The attacker tricks the user into submitting a comment about a link or site, which will then be posted to his/her wall.
- Fake Apps – Users are invited to subscribe to an application that appears to be integrated for use with a social network. The bogus application is designed to harvest user data.
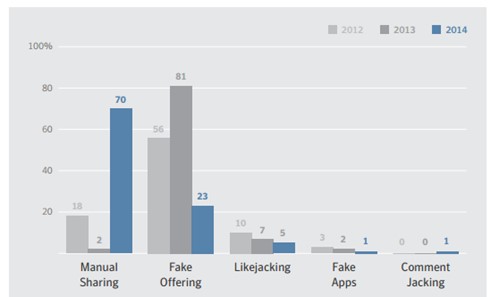 Figure 1 – Social Media scams (Internet Security Threat Report 2015)
Figure 1 – Social Media scams (Internet Security Threat Report 2015) Figure 2 – Social Media Frauds (Social Media scams (Internet Security Threat Report 2015)
Figure 2 – Social Media Frauds (Social Media scams (Internet Security Threat Report 2015)
Another threat to carefully consider when using social media is the malicious mobile application. The diffusion of the “bring your own device” (BYOD) policies is encouraging promiscuous usage of mobile devices at work. While BYOD can lead to increased productivity, it also has the potential to open company asset to cyber attacks. Employees could use apps that hide malicious code or that lack security by design and which, could be exploited to gain control over the mobile device. Malicious mobile apps could allow attackers to steal corporate data and to access repository and services available for employees.
The experts at the Veracode security firm recently conducted an interesting analysis that led to this disconcerting conclusion about the promiscuous use of mobile devices in workplace. Veracode scanned hundreds of thousands mobile apps installed in their corporate mobile environment; some of these companies had 35 mobile gambling apps in their environment. The problem with these gambling apps is once again that they enlarge the surface of attack of the organization by leaving employees mobile open to cyber attacks.
The circumstance is dangerous because it is likely that employees use the same mobile device to access corporate social media and repositories. The researchers discovered critical vulnerabilities that could lead hackers to gain access to the mobile running the gambling app, then access corporate emails, social media accounts, and call history and collect any kind of data from corporate repositories.
The scenarios described could expose the reputation of companies to serious risks. Every scam described could allow hackers to steal sensitive data from a company or take over its social media profiles, a circumstance that could have serious consequences.
Dealing with account takeover and hijack, the most interesting case is represented by the hack of the Twitter account of the Associated Press (AP). The hackers used the AP account to spread the fake news of a cyber attack on the White House that injured the President Obama, the Tweet caused the panic on Wall Street and sent the U.S. stock market into freefall.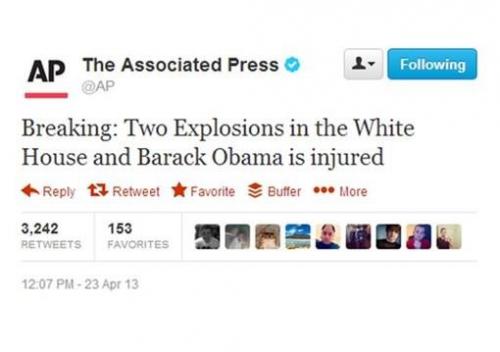 Figure 3 – AP Twitter account hacked
Figure 3 – AP Twitter account hacked
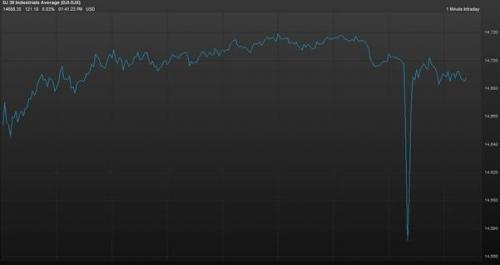 Figure 4 – Effects on Stock Exchange of the AP hack
Figure 4 – Effects on Stock Exchange of the AP hack
Social Media Threats and Risks
We have discussed threats for users of social media services and related risks of exposure, before the introduction of countermeasures; let’s try to display them in a schematic way:
- Data Breach
- Identity theft
- System downtime
- Exposure of the company and its employees data through account hijacking,
- Use of unauthorized social media account, sharing of unapproved content
- Customer backlash/adverse legal actions
- Exposure of company information assets
- Targeted phishing campaign on customers or employees
- Use of personal accounts to communicate corporate owned information assets
- Reputational damage
- Privacy violation
- Copyright infringement
- Customer backlash/adverse legal actions
- Exposure of customer information
Organization Social Media Security Policy
Now that we have highlighted the principal threats for organizations that open their business to the social networks, let’s see how a security policy can address the major social media security threats. An organization must institute a policy to regulate employee access and establish guidelines for appropriate behavior of staffers when dealing with social media.
Policies must specifically address security issues, but not only those! A social media policy has to define the correct posture of the company on the social media by establishing, for example, what can and cannot be shared and communicated through these powerful platforms.
Once a policy is adopted by the organization, it needs to be continuously reviewed and, if necessary, updated and enforced according to the evolution of cyber threats and new needs of the company. The principal elements to consider defining a social media security policy are listed in the following list:
- End-user device security
- Enforce Authentication Best Practices
- Phishing Prevention
- Malware Prevention
- Privacy Protection
The above items must be properly addressed by organizations that intend to protect their assets from threats exploiting social media as an attack vector.
The first line of protection against threats over social networks must be implemented in an end-user machine; this means that employees must be trained to adopt a secure posture to protect the devices they use to access social media accounts. It is essential to educate users on the best practices to follow in order to protect their machines (desktops, laptops, mobile devices). Users must protect their desktop and mobile devices by enabling password-protected screen savers and locking them when they walk away from them.
All the devices must have screensaver timeouts; in this way, if the user leaves the system, the password-protected screensaver comes up after a specific interval of time, preventing unauthorized physical accesses. Do not forget that a threat agent could also be an insider or any occasional guest that accesses the organization or that has the possibility to access the user’s device left unguarded. An unauthorized access to a user’s computer or laptop could allow an ill-intentioned person to install a RAT or any other spyware and harvest user credentials. Similar malware could also allow an attacker to impersonate victims over social media by stealing their credentials.
Another element to address in a security policy for social media is the authentication of employees to the social network accounts. Take care to separate the use of a personal account from the corporate account; their simultaneous use could generate confusion and result in data leakage.
Organizations have to enable two-factor authentication for the accounts of the principal social network they use. Another critical concern is the password security; employees must choose strong passwords, avoiding to share and not properly protect them.
Experts suggest maintaining a different password for each social media account, limiting its knowledge only to staffers explicitly authorized by the social media policy. Unfortunately, the wrong habit of using the same credentials across multiple internet services is quite common in any organization and must be discouraged by a specific policy.
The list of threats to social media users is quite long. Phishing and spear-phishing attacks are still considered among the most dangerous cyber threats for business social media accounts. Phishing attacks exploiting social network are becoming very common and effective, attackers use to share links to phishing pages to gather victim’s credentials.
Because social media tend to create a false sense of intimacy on the Internet, employees are more exposed to any kind of social engineering attack. Users are often quick to accept messages purporting to be from friends, business partners, or organizations that propose the participation in conferences or commercial offers. Such messages often have enticing subject lines or contents, leading victims to perform actions that could open the doors to the attackers, such as downloading and running applications, or opening attachments. If staffers have doubts about the origin of a message or about its authenticity, it could be prudent to contact the sender by an external channel, by phone or in person.
The unique way to prevent social engineering attacks is to provide specific security training to the employees to explain them various phishing attack scenarios and the way to mitigate the risks of exposure of corporate sensitive information.
Another serious threat for organizations that use social media is represented by malicious code. Malware could be used to steal social network credentials of the target organization and impersonate it for various illegal activities, such as malware diffusion, fake news, and much more.
Organizations need to install anti-malware solutions on the end-user devices and ensure that all the software and security solutions must be up-to-date. Also, in this case, the awareness of cyber threats is essential to prevent incidents. Employees must know the threats and the way to avoid them; for example, not clicking on links shared by friends or downloading files from a web site.
Let’s close with the major concern to almost any organization: the sharing of confidential or sensitive information by employees on the Internet. Organizations such as the SANS Institute suggest the adoption of an acceptable use policy for computer end-users that prohibit employees from revealing any company confidential or proprietary information, trade secrets, or any other material covered by the company’s confidential Information policy when engaged in blogging and posting over social media.
Employees need to correctly manage privacy settings and staffers’ social-media accounts should be configured in order to ensure their maximum protection. Organizations and employees in charge of the management of social media accounts should not rely on the default settings.
A crucial concern for companies when dealing with social networks is the disclosure of confidential information. There are various factors that increase the risk of exposure of confidential data through the social media platforms. We have highlighted the false sense of familiarity induced by social network that can lead employees to disclose secret information. Employees may be inclined to reveal pieces of information that could be gathered by threat actors that, by being cross-referenced with open source data, could allow access to sensitive corporate information.
A Real Case
It is not easy to explain to employees what “enlarge surface of attack” means when companies and employees are very active on social media. For this reason, I decided to present to you a recent case that demonstrate the risks of a cyber attack resulting from the exposure on social networks.
Security researchers have uncovered a group of fake recruiting accounts on LinkedIn used for intelligence gathering about security experts. A group of fake recruiter accounts on LinkedIn was exploited by unknown threat actors to send invitations to security professionals in various industries. The fake recruiters attempt to trick victims by using a LinkedIn profile with a picture of an attractive woman but, as explained by experts at Fox-IT, soon after the account details and the picture are changed.
The security professionals targeted in the campaign might receive multiple recruitment invitations per day from the group. The alarm was raised by the expert Yonathan Klijnsma at the Fox-IT security firm a few weeks ago; meanwhile, the Security Advisor from F-Secure, Sean Sullivan, analyzed in detail the fake LinkedIn accounts used by the group. Sullivan discovered that they belong to individuals supposedly working for Talent Src (Talent Sources).
The bogus accounts used images of a number of legitimate LinkedIn accounts or pictures taken from Instagram. Sullivan noticed that the logo of the company Talent Scr was also a fake; it seems that the same bogus company has used a Twitter account that hasn’t been updated since January and that posted just two tweets. Which is the goal of the fake recruiting group? The threat actor behind the group is trying to uncover the entire network of connections of cyber security experts. he exploitation of social networks for intelligence gathering, especially professional social media like LinkedIn, is very common.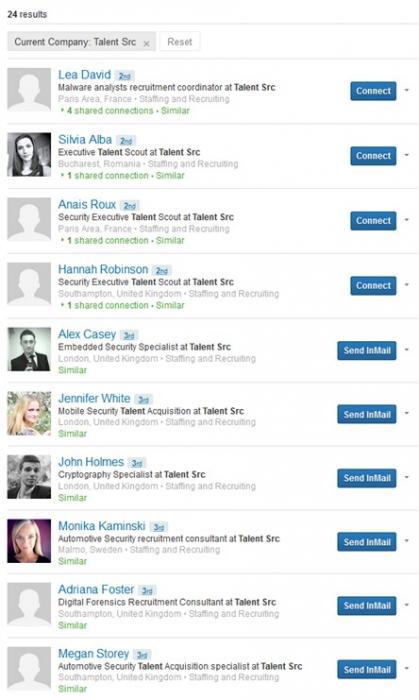 Figure 5 – Bogus Recruiter account used for Intelligence Gathering activities on LinkedIn
Figure 5 – Bogus Recruiter account used for Intelligence Gathering activities on LinkedIn
No Social Media Security Policies … the Greatest Risk
The case proposed is just the tip of the iceberg of the vast amount of attacks that rely on social network to harvest sensitive information and businesses are particularly exposed to these threats.
The damage caused by a cyber attack could be dramatic for a company; social networks could represent the entry point for bad actors that could use them for intelligence gathering or to direct abuse of the brand of the organization damaging its reputation.
The increasing openness of companies with social networks urges the adoption of a strong security posture of the organization and its employees. The key factor for the successful use of social media are awareness training and the adoption of social media security policies.
Any business without a social media policy runs the serious risk of enlarging its surface of attack. A social media policy outlines acceptable behaviors for employees that use social media at work, in order to limit exposure to threats of the company information.
Social media policies also require adequate training for the employees of the organization in order to instruct them in responding security threats exploiting the social networks.
Social media are a powerful business instrument for companies and they can be extremely effective in helping organizations expand their customer base, increase the brand reputation, and improve their products. However, companies cannot underestimate the risks for their organizations’ they have to increase within the organization the knowledge about the threats and potential risks for the business. Once the security risks are identified, the company has to define an action plan to maximize the benefits that social media provides to the business.




